Definition and Conceptual Foundations
Crypto‑agility refers to an organization’s ability to rapidly and securely transition between cryptographic algorithms, protocols, and configurations as security requirements evolve. This capability is essential for responding to algorithmic vulnerabilities, cryptographic deprecations, regulatory changes, and emerging threats such as quantum computing.
According to the draft NIST Cybersecurity White Paper (CSWP) 39, “On the Road to Crypto-Agility,” crypto-agility is defined as:
“The capabilities needed to replace and adapt cryptographic algorithms, parameters, processes, and technologies without introducing unacceptable security risks and without disrupting the normal operation of systems and business processes.”
- The identification and inventory of all cryptographic assets in an environment (e.g., keys, certificates, libraries, and protocol configurations).
- The policy-driven management of cryptographic upgrades and transitions
- The ability to automate detection, assessment, and remediation of cryptographic risks at scale.
- The governance and reporting required to demonstrate security posture and compliance readiness.
Algorithms
Why Crypto‑Agility Has Become a Strategic Imperative
Historically, cryptographic transitions have been infrequent and slow. For example:
- The transition from the Data Encryption Standard (DES) to Triple DES (3DES), and later to the Advanced Encryption Standard (AES), took years to achieve industry-wide adoption.
- The migration from SHA‑1 to SHA‑2 faced prolonged implementation timelines, despite known vulnerabilities in SHA‑1.
- The deprecation of outdated TLS versions (1.0, 1.1) and associated cipher suites required coordinated efforts across browser vendors, infrastructure providers, and enterprise IT.
- Quantum resistance: Transitioning from legacy asymmetric algorithms to PQC algorithms such as CRYSTALS-Kyber (for key encapsulation) and CRYSTALS-Dilithium (for digital signatures).
- Regulatory compliance: Meeting mandates from NIST, CISA, and DHS requiring algorithm upgrades, inventory documentation, and transition planning.
- Operational continuity: Avoiding outages or performance degradation during cryptographic migrations.
- Incident response: Reacting rapidly to the discovery of vulnerabilities or the compromise of cryptographic mechanisms.
Key Rotation
Algorithm Switching
Cryptographic Inventory
Policy Enforcement
Dimensions of Crypto‑Agility
- Modularity
Systems must be designed to isolate cryptographic logic from application code, allowing algorithms to be substituted without reengineering. This applies at the level of APIs, libraries, and protocols. - Cryptographic Inventory
Organizations must maintain an accurate and continuously updated record of where cryptography is used – across applications, endpoints, cloud environments, and embedded systems. - Algorithm Negotiation
Protocols should support runtime negotiation of algorithm preferences (e.g., through cipher suite declarations in TLS), enabling smoother transitions and hybrid deployments. - Automation
Manual tracking and updating of cryptographic assets does not scale. Automation is essential for key rotation, certificate renewal, protocol enforcement, and compliance validation. - Policy and Governance
Crypto-agility must operate within an enterprise governance framework that defines approved algorithms, key sizes, transition timelines, and exceptions. - Resilience
Systems must continue operating securely throughout the migration process, supporting hybrid cryptography and enabling rollback in case of failure. - Compliance Reporting
Organizations must be able to demonstrate to internal stakeholders, regulators, and auditors that cryptographic policies are being followed and that cryptographic exposure is minimized.
A Paradigm Shift in Cryptographic Engineering
- The U.S. Department of Homeland Security’s Post-Quantum Cryptography Roadmap explicitly identifies crypto-agility as an essential capability for federal systems.
- The Office of Management and Budget (OMB) has directed federal agencies to inventory their cryptographic systems and prepare for quantum-safe transitions.
- The Cybersecurity and Infrastructure Security Agency (CISA) has published technical guidance for achieving cryptographic visibility and implementing crypto-agility practices in critical infrastructure sectors.
Summary
Crypto-agility is the capability to dynamically manage cryptographic change at scale. It addresses both the technical and governance challenges associated with algorithmic transitions, inventory discovery, automation, and compliance. As quantum threats grow and regulatory expectations rise, crypto-agility will serve as the cornerstone of cryptographic resilience.
In subsequent sections, we will examine the historical challenges of cryptographic transitions, the architectural components required to implement agility, and the practical steps organizations can take to prepare today.

Historical Context and Transition Challenges
Cryptographic Change: Rare, Complex, and Often Delayed
Examples of Past Cryptographic Migrations
-
DES to 3DES to AES
The original Data Encryption Standard (DES), introduced in the 1970s, became vulnerable to brute-force attacks by the late 1990s. The interim solution - Triple DES (3DES) - extended DES's lifespan but introduced performance limitations. In 2001, the Advanced Encryption Standard (AES) was adopted as the new standard. Despite this, widespread adoption of AES took several additional years, and many legacy systems continued to rely on 3DES well into the 2010s. -
SHA-1 to SHA-2 to SHA-3
SHA-1 was widely used for digital signatures, certificate authorities, and cryptographic hashes in software and protocols such as SSL/TLS and Git. As early as 2005, cryptographic researchers demonstrated weaknesses in SHA-1, yet the transition to SHA-2 (and later SHA-3) was slow and inconsistent. Even after formal deprecation by NIST, SHA-1 remained in use in critical systems for years. -
TLS 1.0/1.1 to TLS 1.2/1.3
The Transport Layer Security (TLS) protocol underwent major revisions to address vulnerabilities in legacy versions. TLS 1.0 and 1.1 were deprecated in 2020, yet many organizations struggled to migrate, often due to embedded systems, third-party dependencies, or insufficient understanding of protocol negotiation mechanisms. Transitioning to TLS 1.3 - despite its security benefits - has posed interoperability and implementation challenges across enterprises.
Structural Barriers to Agile Cryptographic Transitions
1. Legacy Dependencies and Backward Compatibility
Modern IT environments are composed of complex interdependencies: applications that rely on legacy libraries, devices with hardcoded cryptographic implementations, and third-party components whose security posture is opaque. Backward compatibility is often prioritized over cryptographic modernization, creating persistent exposure to deprecated algorithms.
In many cases, applications assume the availability of specific algorithms or key formats and are not designed to support substitution without code modification. For example, a system designed around RSA key exchange may not be compatible with lattice-based post-quantum algorithms, even at the protocol level.
2. Fragmentation Across Infrastructure and Protocols
Cryptography is implemented at multiple layers of the technology stack – from hardware and firmware, to operating systems, to application-layer protocols such as TLS, IPsec, S/MIME, and SSH. These layers are often maintained by different teams, vendors, or business units, creating fragmentation and inconsistency in cryptographic policy enforcement.
Even identifying where cryptography is used – what libraries, configurations, or embedded keys are present – can be a substantial challenge in distributed, cloud-native, or hybrid environments.
Many modern cryptographic algorithms, especially post-quantum candidates, involve larger key sizes and higher computational overhead. This poses performance trade-offs, particularly in constrained environments such as IoT devices, embedded systems, or high-throughput network services.
Organizations may delay transitions due to concerns about latency, resource consumption, or application compatibility. Without appropriate benchmarking and risk prioritization, these concerns can stall necessary upgrades.
Cryptographic change often requires coordinated updates across systems, services, and stakeholders. Without automation, this coordination becomes error-prone and labor-intensive. Manual processes – such as locating hardcoded keys, updating cipher suite configurations, or rotating certificates – introduce the risk of misconfiguration, downtime, or incomplete remediation.
Moreover, cryptographic assets are rarely tracked with the same rigor as other enterprise assets. Organizations may lack centralized inventories of where cryptography is implemented, what algorithms are in use, and whether those implementations are up to date.
4. Operational Complexity and Lack of Automation
Cryptographic change often requires coordinated updates across systems, services, and stakeholders. Without automation, this coordination becomes error-prone and labor-intensive. Manual processes – such as locating hardcoded keys, updating cipher suite configurations, or rotating certificates – introduce the risk of misconfiguration, downtime, or incomplete remediation.
Moreover, cryptographic assets are rarely tracked with the same rigor as other enterprise assets. Organizations may lack centralized inventories of where cryptography is implemented, what algorithms are in use, and whether those implementations are up to date.
The Emerging Post-Quantum Transition Challenge
- Identification of all systems relying on quantum-vulnerable algorithms (e.g., RSA, ECC).
- Selection of post-quantum counterparts appropriate for each use case.
- Modification of protocol implementations, library bindings, and application dependencies.
- Testing for interoperability, performance, and security.
- Development of rollback strategies and contingency plans.
Toward a More Agile Model
Crypto-agility enables this transformation. It repositions cryptographic management as a dynamic, ongoing capability rather than a one-time engineering effort. By embedding agility into system design and governance processes, organizations can minimize disruption, accelerate adoption of secure standards, and ensure resilience against future cryptographic shifts.

Core Components of Crypto‑Agility
Cryptographic Inventory & Discovery
Know every cryptographic asset you have.
Key and Certificate Lifecycle Management
Manage creation, rotation, renewal, and expiry.
Modular Cryptographic APIs & Protocols
Easily swap or upgrade crypto algorithms without breaking apps.
Hybrid Algorithm Support (PQC + classical)
Use classical + post-quantum cryptography together for smoother transitions.
Governance, Monitoring, and Automation
Policies, monitoring, and automated responses to threats or changes.
Crypto-agility is not a monolithic capability but rather a system of interconnected practices and architectural principles that collectively enable secure, adaptable cryptographic infrastructure. This section examines the foundational components of crypto-agility, as defined by NIST, QuSecure, and leading cryptographic engineering frameworks. These components form the operational baseline upon which agile cryptographic posture is built and maintained.
1. Modularity and Algorithm Abstraction
NIST emphasizes the importance of modularity in its guidance, noting that:
“Cryptographic implementations should enable substitution or reconfiguration of algorithms with minimal changes to the system.”
- Use of cryptographic libraries with clearly defined APIs that allow algorithm parameters to be modified without recompilation.
- Protocol implementations (e.g., TLS, SSH) that support runtime negotiation of cipher suites.
- Application architectures that separate cryptographic operations from data-handling and business logic layers.
Without modularity, algorithm transitions require invasive application changes and pose significant operational risk.
2. Accurate and Continuous Cryptographic Inventory
Such an inventory should include:
- Algorithm usage (e.g., RSA, AES, SHA‑1) across all layers of the stack.
- Key and certificate types, locations, and expiration timelines.
- Protocol configurations and supported cipher suites.
- Cryptographic libraries and their associated software versions.
- Device- or hardware-specific cryptographic functions (e.g., TPMs, HSMs, firmware encryption).
NIST recommends establishing this inventory as a prerequisite for any transition planning. Tools such as passive network monitoring, software bill of materials (SBOM) analysis, and agent-based scanning can assist in generating and maintaining visibility.
Inventory systems must also classify assets based on risk and priority, enabling organizations to focus remediation efforts on High-Value Assets (HVAs) – those systems handling the most sensitive data, highest transaction volumes, or most mission-critical functions.
3. Hybrid Cryptographic Implementations
Hybrid implementations are endorsed by NIST and recommended by security researchers as a pragmatic bridge between legacy and future-ready systems. These configurations provide cryptographic redundancy while allowing for interoperability with existing systems.
Examples include:
- Dual key exchange mechanisms (e.g., combining ECDH and Kyber)
- Compound digital signatures (e.g., concatenating ECDSA and Dilithium signatures).
- Protocol extensions that support negotiation of both classical and PQC algorithms.
- Cryptographic libraries and their associated software versions.
- Device- or hardware-specific cryptographic functions (e.g., TPMs, HSMs, firmware encryption).
NIST recommends establishing this inventory as a prerequisite for any transition planning. Tools such as passive network monitoring, software bill of materials (SBOM) analysis, and agent-based scanning can assist in generating and maintaining visibility. Inventory systems must also classify assets based on risk and priority, enabling organizations to focus remediation efforts on High-Value Assets (HVAs) – those systems handling the most sensitive data, highest transaction volumes, or most mission-critical functions.
4. Automated Lifecycle Management of Keys and Certificates
Automated lifecycle management includes:
- Policy-based key rotation schedules.
- Certificate issuance and renewal via integrated PKI or external CAs.
- Expiry monitoring and alerting.
- Revocation tracking (e.g., OCSP, CRLs).
- Enforcement of key strength, algorithm usage, and validity constraints.
Tools that automate these functions – integrated into enterprise orchestration platforms or identity and access management (IAM) systems – reduce the likelihood of lapses, misconfigurations, and outages due to expired or compromised credentials.
Lifecycle automation is particularly critical in large-scale environments where thousands of keys or certificates may be deployed across cloud services, endpoints, APIs, and embedded systems.
5. Policy Governance and Enforcement
Policy governance includes:
- Definition of approved algorithms and key lengths.
- Rules for deprecated or banned algorithms (e.g., MD5, RC4).
- Transition timelines for algorithm replacement.
- Requirements for hybrid or post-quantum configurations.
- Mapping to external standards such as NIST SP 800‑57, SP 800‑131A, and future PQC profiles.
These policies must be centrally maintained, programmatically enforced, and auditable. Governance ensures that agility is not ad hoc but instead guided by risk prioritization, compliance obligations, and strategic objectives.
Policy enforcement mechanisms can include configuration baselines, policy-as-code implementations, CI/CD pipeline validation, and periodic cryptographic hygiene scans.
6. Resilience and Runtime Adaptability
This includes:
- Support for dynamic algorithm switching without service downtime.
- Rollback capabilities in the event of interoperability failures.
- Use of version-controlled cryptographic modules or containers.
- Runtime metrics on cryptographic performance and failure rates.
Cryptographic resilience minimizes operational risk during migrations and reduces the blast radius of implementation errors. It ensures that cryptographic modernization efforts do not create new availability or security issues in the process of solving old ones.
7. Monitoring, Testing, and Validation
This includes:
- Periodic validation of cipher suite configurations across endpoints.
- Library version tracking and vulnerability scanning.
- Performance benchmarking for newly deployed algorithms.
- Logging and telemetry for cryptographic operations.
- Independent security assessments or third-party validation.
Monitoring infrastructure must also detect anomalies that may indicate misuse or failure of cryptographic functions – such as excessive handshake failures, certificate errors, or unexpected fallback to weaker algorithms.
Summary
In the next section, we will examine the frameworks and maturity models that organizations can use to assess and improve their crypto-agility posture over time.
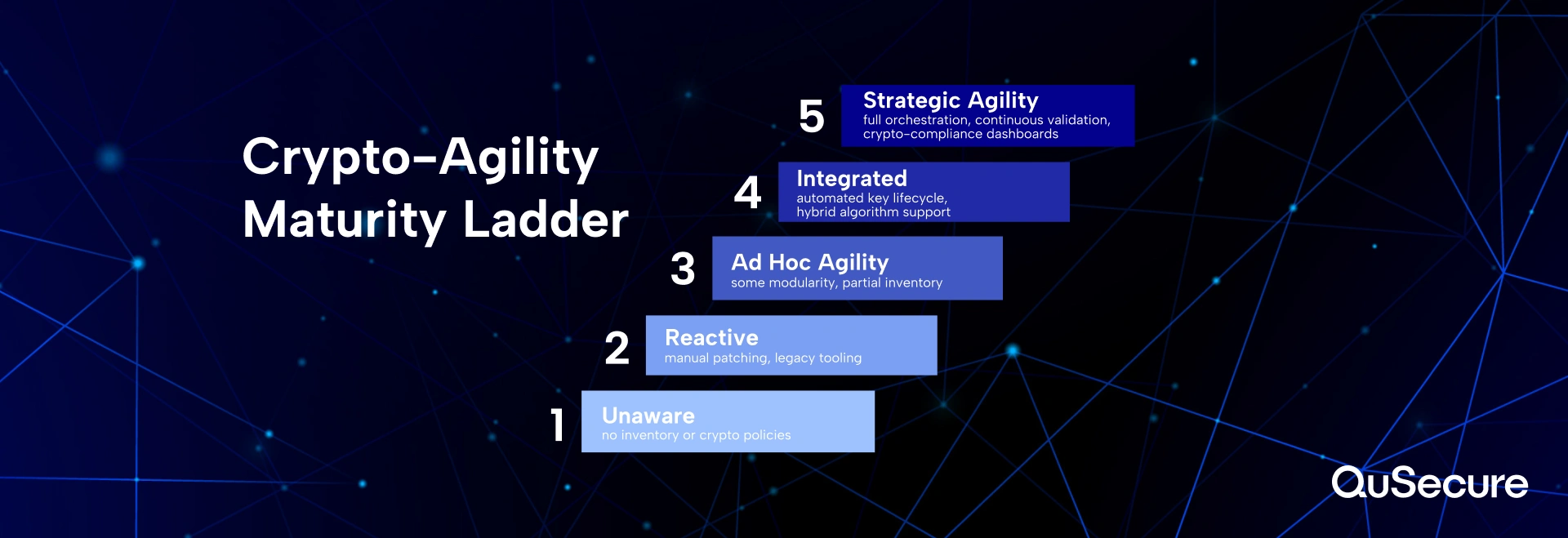
Frameworks and Maturity Models
As crypto-agility evolves from a technical aspiration to a strategic imperative, structured frameworks have emerged to help organizations assess their current posture and systematically advance their capabilities. These models offer a shared vocabulary and roadmap for improving cryptographic adaptability in alignment with operational risk, regulatory mandates, and organizational maturity.
While no single global standard currently governs crypto-agility, several well-researched maturity models and governance frameworks have been published by academic institutions, cybersecurity vendors, and regulatory agencies. Each contributes to a growing consensus on the foundational elements of agile cryptographic infrastructure.
1. Crypto-Agility Maturity Model (CAMM)
-
Level 0 – Unaware:
No formal awareness of cryptographic dependencies or risks. No inventory or governance structures in place. Cryptography is embedded in code and managed in an ad hoc fashion. -
Level 1 – Aware:
The organization has begun cataloging cryptographic assets and recognizes algorithm-related risks but lacks centralized policy or consistent management practices. -
Level 2 – Controlled:
Cryptographic assets are inventoried, policies are documented, and controls are in place for key lifecycle management. However, transition capabilities are limited and manual. -
Level 3 – Agile:
Cryptographic systems are modular, algorithm substitution is possible without major redevelopment, and cryptographic transitions are governed by policy and automation. -
Level 4 – Resilient:
Crypto-agility is embedded into the organization’s design and operations. Continuous monitoring, risk-based algorithm selection, and integration with CI/CD pipelines enable real-time adaptation to evolving threats or standards.
2. Software-Defined Cryptography (SDC)
Key elements of SDC include:
- Cryptographic policy as code, integrated into build and deployment pipelines.
- API-based orchestration of key provisioning, algorithm selection, and certificate issuance.
- Role-based access control (RBAC) over cryptographic decisions.
- Real-time cryptographic telemetry to inform operational policy.
SDC aligns closely with the needs of modern, cloud-native enterprises. It recognizes that agility is not simply the result of better libraries, but of architectural separation, developer tooling, and governance integration.
3. Six Dimensions of Crypto-Agility (Näther et al.)
1. Inventory – the ability to identify where and how cryptography is used.
2. Substitutability – the capability to replace algorithms and parameters.
3. Configurability – the flexibility to modify cryptographic settings without code changes.
4. Automation – the degree of process automation in key and cert management.
5. Monitoring – the ability to observe, log, and assess cryptographic events.
6. Governance – the existence of policy frameworks and decision-making authority.
This model reinforces the interdisciplinary nature of crypto-agility. Technical controls must be supported by procedural mechanisms, organizational alignment, and continuous assurance.
4. NIST Guidance and Pre-Standardization Efforts
- Separation of duties between algorithm selection, implementation, and deployment.
- Support for algorithm negotiation in protocols to enable smooth transitions.
- Dependency mapping between cryptographic components and business functions
- Support for hybrid deployments during post-quantum transitions.
- Prioritized remediation of High-Value Assets (HVAs) based on mission criticality.
NIST encourages organizations to embed crypto-agility into security architecture, development processes, and supply chain risk management. While detailed benchmarks are still forthcoming, these foundational documents will likely shape future standards and assessment tools.
5. Vendor-Based Reference Models
- Discovery engines for cryptographic asset identification.
- Centralized dashboards for cryptographic posture reporting.
- Policy-driven key and certificate orchestration.
- Integrations with SIEM, SOAR, and identity platforms.
While these tools vary in scope and sophistication, they reflect an industry shift toward systematizing cryptographic governance and supporting operational resilience..

Summary
By adopting and adapting frameworks such as CAMM, Software-Defined Cryptography, and NIST’s foundational guidance, organizations can move from passive risk awareness to active cryptographic readiness. In the next section, we examine how to apply these principles in practice – translating theory into actionable steps for building crypto-agility across systems and teams.
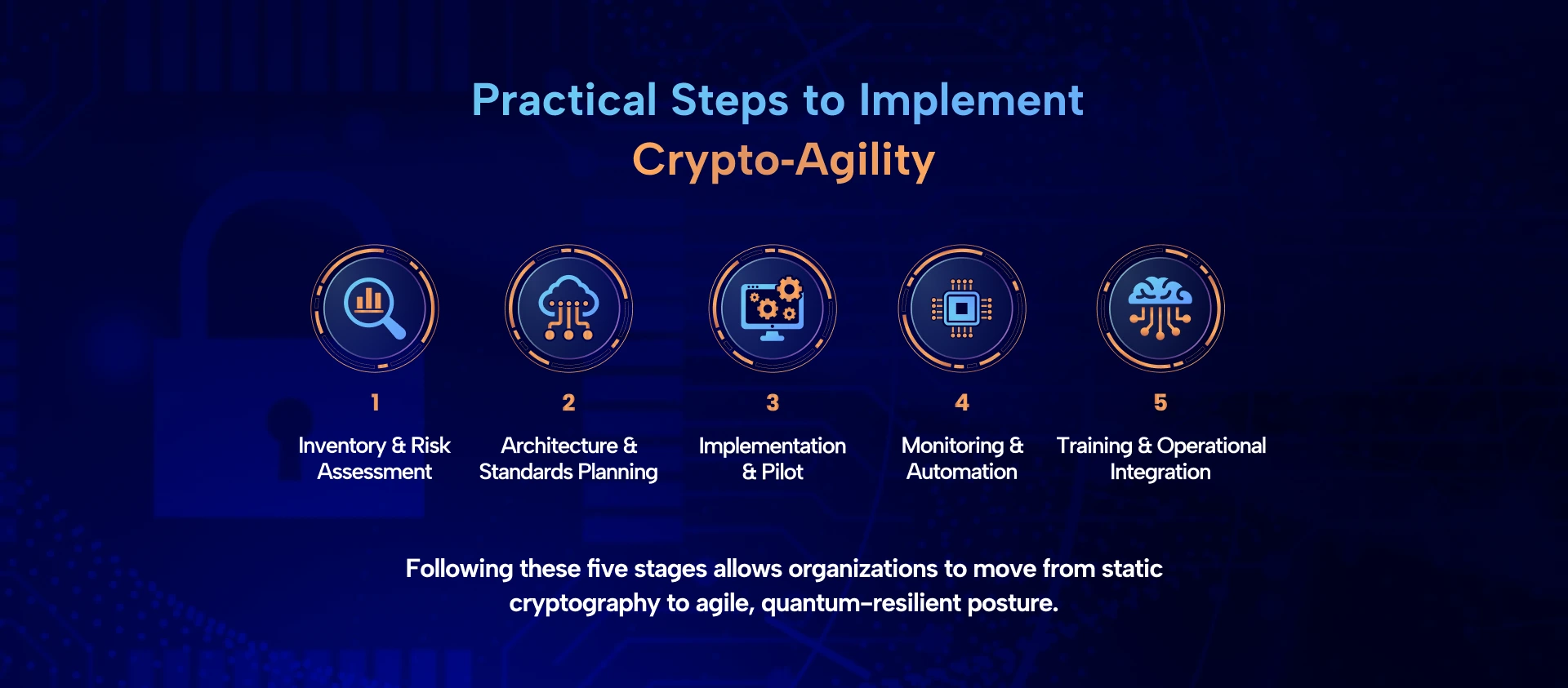
Practical Steps to Implement Crypto‑Agility

Phase 1: Inventory and Risk Assessment

-
Cryptographic Asset Discovery
Identify all systems, applications, and devices using cryptographic algorithms, keys, or protocols. This includes hardcoded cryptography in legacy systems, cryptographic functions embedded in third-party libraries, and configurations across cloud and on-prem environments. -
Algorithm Classification and Versioning
Catalog algorithm types (e.g., RSA, ECDSA, AES, SHA‑1, SHA‑2), their intended purpose (e.g., encryption, signing), and their cryptographic strength or vulnerability based on current guidance. -
Protocol Surface Mapping
Document where protocols such as TLS, SSH, IPsec, and S/MIME are deployed, along with their supported cipher suites and fallback behavior. -
High-Value Asset (HVA) Prioritization
Classify systems by business criticality, data sensitivity, and network exposure. Prioritize cryptographic upgrades where compromise would have the greatest impact. -
Gap and Vulnerability Analysis
Determine where cryptographic use is outdated, insecure, misconfigured, or undocumented. Leverage standards such as NIST SP 800‑131A to assess algorithm deprecation status.
An effective inventory phase enables organizations to move from anecdotal or partial awareness to a full-spectrum view of their cryptographic posture.
Phase 2: Architecture and Standards Planning
With an accurate baseline established, the next step is to architect a future-ready cryptographic design – one that supports modularity, automation, and graceful transition.

Key focus areas include:
-
Define Cryptographic Standards and Policy
Formalize which algorithms are approved, deprecated, or pending transition. Document key sizes, certificate formats, and lifecycle requirements. Establish hybrid strategies (e.g., dual-mode TLS configurations) for post-quantum readiness. -
Design Modular Cryptographic Interfaces
Refactor or re-architect applications and services to separate cryptographic logic from core functionality. Adopt standardized APIs (e.g., PKCS#11, OpenSSL, BoringSSL) and vendor-agnostic libraries. -
Enable Algorithm Negotiation in Protocols
Ensure protocols can gracefully support new algorithms during handshakes and do not rely on hardcoded or static cipher suites. -
Establish a Governance Framework
Define roles, responsibilities, and escalation paths for cryptographic decisions. Integrate cryptographic standards into enterprise security policy and software development life cycle (SDLC). -
Engage Stakeholders Across IT and Risk Functions
Coordinate among CISOs, IT architects, application developers, compliance officers, and procurement teams to ensure alignment and budget allocation.
A clear architectural and governance plan reduces implementation risk, streamlines procurement, and positions the organization for long-term agility.
Phase 3: Implementation and Pilot Programs

Key activities:
-
Deploy Cryptographic Inventory and Discovery Tools
Use specialized platforms (e.g., cryptographic scanners, SBOM analyzers, QuSecure Recon) to continuously update the inventory and detect algorithm usage drift. -
Introduce Crypto-Orchestration Platforms
Pilot orchestration engines capable of managing algorithm transitions, certificate rotation, and key lifecycle workflows. Ensure integration with identity and policy systems. -
Implement Hybrid Cryptography Configurations
Select applications that support dual-algorithm mode (classical + PQC) and evaluate interoperability, performance, and system behavior. Focus initial efforts on externally facing services and APIs. -
Refactor Code and Protocol Dependencies
Where cryptography is hardcoded or incompatible with target algorithms, refactor codebases to accept dynamic algorithm input or updated libraries. -
Validate Operational Impact
Conduct performance testing, failure mode analysis, and regression testing. Validate logging and alerting for cryptographic events.
Implementation is not a one-time event but a continuous process. Pilot environments should include rollback plans and detailed logging to accelerate learning and iteration.
Phase 4: Monitoring, Automation, and Continuous Improvement

Recommended actions:
-
Automate Certificate and Key Lifecycle Tasks
Use policy-driven tools to handle issuance, renewal, rotation, and revocation. Avoid manual credential management wherever possible. -
Monitor Algorithm Usage and Deviations
Set up alerts for deprecated algorithm usage, expired certificates, and failed cryptographic operations. Ensure telemetry includes cipher negotiation outcomes and cryptographic module health. -
Benchmark New Algorithm Performance
Collect latency, throughput, and CPU/memory utilization metrics for classical and post-quantum algorithms. Use this data to guide hardware scaling or application optimization. -
Integrate with DevSecOps Toolchains
Embed cryptographic policy checks into CI/CD pipelines, infrastructure-as-code templates, and security configuration management tools. -
Audit and Report on Cryptographic Posture
Maintain dashboards and audit logs for internal stakeholders and external regulators. Demonstrate compliance with FIPS, NIST, or sector-specific mandates.
Phase 5: Organizational Culture and Training
-
Develop Training Programs for Developers and Engineers
Focus on secure cryptographic practices, library selection, protocol negotiation, and crypto hygiene. Emphasize agility as a design requirement, not a future feature. -
Run Incident Response Drills Focused on Cryptographic Events
Prepare for scenarios involving algorithm compromise, certificate compromise, or post-quantum zero-day vulnerabilities. Define escalation protocols and decision frameworks. -
Incorporate Crypto-Awareness into Risk Governance
Ensure that cryptographic posture is tracked and discussed in security reviews, IT audits, and board-level risk reports. -
Foster Cross-Functional Communication
Bridge the gap between cryptography, application development, compliance, and procurement through shared goals and metrics. -
Promote Agility as a Strategic Advantage
Maintain dashboards and audit logs for internal stakeholders and external regulators. Demonstrate compliance with FIPS, NIST, or sector-specific mandates.
Summary
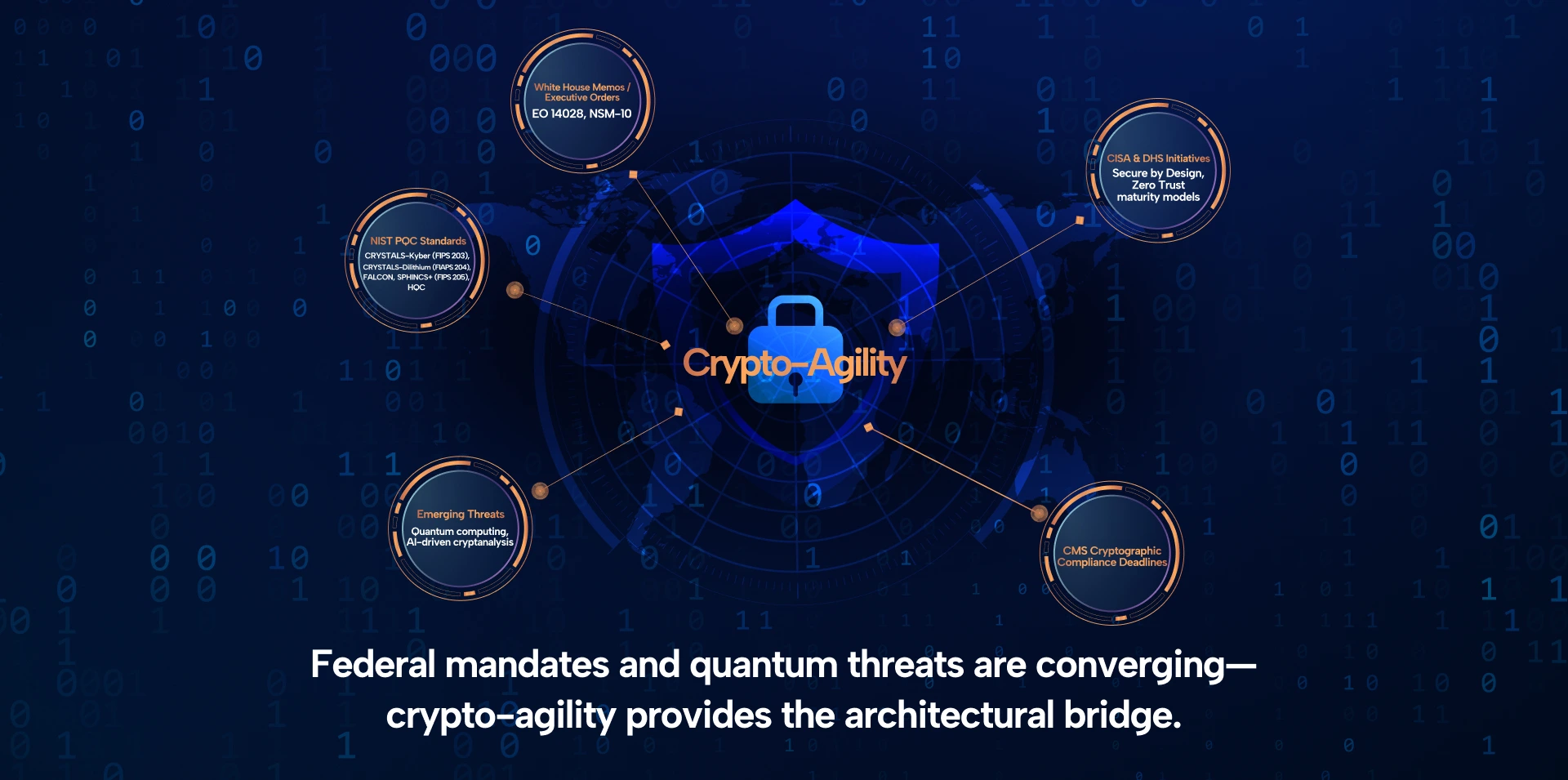
Post‑Quantum & Regulatory Drivers
NIST’s Post-Quantum
Cryptography (PQC) Initiative

- CRYSTALS-Kyber for public key encryption and key encapsulation mechanisms (KEM)
- CRYSTALS-Dilithium, FALCON, and SPHINCS+ for digital signatures
These algorithms were chosen for their resistance to attacks from both classical and quantum computers, based on rigorous cryptanalysis, implementation studies, and performance evaluations.
- Design systems to support algorithm substitution without downtime
- Enable hybrid modes (classical + PQC) during the transition
- Inventory all cryptographic use cases, not just external endpoints
- Focus initially on High-Value Assets (HVAs) with the greatest data exposure and operational risk
DHS and CISA: National Security Directives

- Completing a cryptographic discovery and inventory phase (initially by May 2023)
- Submitting PQC readiness assessments
- Transitioning to NIST-approved PQC algorithms upon final publication
- Reporting annually on cryptographic migration progress
CMS and Sector-Specific Guidance

- Proactive cryptographic algorithm reviews
- Elimination of deprecated ciphers (e.g., SHA‑1, RSA-1024)
- Certificate lifecycle management protocols
- Secure transition plans to quantum-safe algorithms
Global Regulatory Developments

- ENISA (EU Agency for Cybersecurity) has emphasized PQC and crypto-agility in its threat landscape reports.
- The UK’s National Cyber Security Centre (NCSC) has released guidance on PQC and supports hybrid transition models.
- The ISO/IEC JTC 1/SC 27 working group has begun aligning standards with PQC integration, cryptographic key management, and system interoperability.
Risk of Retrospective Decryption (“Harvest Now, Decrypt Later”)

- Long-lifespan data (e.g., medical records, IP portfolios, legal archives)
- Government communications and classified information
- Financial transaction archives and payment infrastructure logs
Summary

Benefits and Trade-Offs
Strategic and Operational Benefits

1. Accelerated Threat Response
- Algorithm substitution with minimal code change
- Certificate re-issuance and revocation automation
- Cipher suite negotiation without rearchitecting applications
2. Regulatory Alignment and Readiness
- Demonstrate cryptographic governance in audits
- Meet evolving mandates from NIST, DHS, CMS, and others
- Position themselves for rapid adoption of post-quantum standards
3. Improved System Resilience
- Simplifies patching and updating
- Isolates cryptographic failures from business logic
- Enables hybrid deployments (e.g., classical + post-quantum) without impacting UX
4. Future-Proofing Long-Lifespan Data
- Early integration of post-quantum algorithms
- Hybrid configurations to hedge against obsolescence
- Migration planning for systems with 10–20+ year data retention requirements
5. Enhanced Visibility and Governance
- Full cryptographic asset inventories
- Real-time visibility into algorithm usage
- Policy enforcement across key lifecycles and protocol configurations
Practical and Architectural Trade-Offs

1. Increased Complexity
- Identifying and abstracting embedded cryptographic calls
- Refactoring legacy systems
- Building compatibility layers for hybrid or transitional algorithms
2. Performance Overhead
- Increased CPU utilization
- Larger payloads in constrained networks
- Longer cryptographic negotiation times
3. Vendor Lock-In and Ecosystem Gaps
- Some vendors support only subsets of required functionality
- Integration with existing CI/CD, SIEM, and identity platforms is limited
- Proprietary solutions may limit flexibility in algorithm choice or implementation
4. Risk of Misconfiguration and Downgrade Attacks
- Misconfigurations (e.g., allowing deprecated algorithms in fallback scenarios)
- Downgrade attacks where an attacker forces use of a weaker ciphe
- Errors in hybrid implementations that undermine security guarantees
5. Organizational Learning Curve
- Low familiarity with post-quantum cryptography
- Gaps in secure cryptographic development practices
- Lack of clear ownership over cryptographic assets
Summary

Future Trends and Research
1. Rise of Software-Defined Cryptography

- Crypto-as-a-Service (CaaS) platforms, enabling organizations to consume cryptographic functionality through secure APIs with dynamic algorithm selection and key rotation.
- Orchestration layers that manage hybrid cipher suites, protocol negotiation, and fallback behavior across applications and services.
- Policy automation engines that enforce algorithm compliance, certificate hygiene, and lifecycle governance in real time.
2. Continuous Cryptographic Assurance

- Real-time telemetry and anomaly detection for cryptographic operations (e.g., sudden use of deprecated algorithms, failed key negotiations)
- Cryptographic health scoring across applications and network segments
- Continuous compliance monitoring for internal standards and external mandates
3. Cryptographic Digital Twins

The concept of digital twins – virtual models of physical systems used in manufacturing and operations – is now being applied to cryptographic environments.
- Key and certificate lifecycles
- Algorithm deployments across services
- Protocol and cipher suite configurations
- Interdependencies between applications, hardware, and third-party libraries
These models allow for scenario planning, change impact analysis, and simulation of algorithm migrations before executing changes in production. This approach supports safe transition to PQC and minimizes operational risk.
4. Maturity Models and Self-Assessment Frameworks

- The Crypto-Agility Maturity Model (CAMM), proposed by Hohm et al., which assesses organizational posture across dimensions such as inventory, policy, architecture, and automation.
- Academic reviews (e.g., Näther et al., 2023) identifying six definitional categories of crypto-agility, leading toward a more standardized vocabulary and evaluative criteria.
- Integration of crypto-agility into broader cyber resilience frameworks, linking algorithm agility to enterprise risk management and business continuity planning.
5. Sector-Specific Guidance and Taxonomies

- Financial services regulators are aligning crypto-agility with operational risk and third-party vendor compliance.
- Healthcare entities are emphasizing data longevity and hybrid algorithm support for electronic health records.
- Telecommunications providers are adopting crypto-agility to secure control plane traffic, subscriber data, and signaling protocols (e.g., 5G core)
- Defense and aerospace organizations are requiring crypto-agility to support multilateral interoperability, key sovereignty, and secure satellite communications.
6. Global Standards and PQC Interoperability

- TLS and IPsec hybrid specifications, formalizing how classical and quantum-resistant algorithms are paired and negotiated
- Certificate formats and root-of-trust updates to accommodate larger key sizes and dual-signature chains
- Library standardization and FIPS validation pathways for emerging PQC algorithms, especially CRYSTALS-Kyber and Dilithium.
7. Vendor Ecosystem Consolidation

- Convergence of tools into unified crypto-agility platforms
- Integration with broader security ecosystems including SIEM, SOAR, and identity access management (IAM)
- Standard APIs and schema definitions for cryptographic discovery, inventory, and telemetry
Summary
In the next section, we will synthesize these insights into a practical roadmap – outlining a step-by-step path to achieving and maintaining crypto-agility in complex enterprise environments.Crypto-agility is moving beyond its initial focus on algorithm substitution and post-quantum readOrganizations that align their strategy with these trends will be better equipped to handle regulatory change, technology disruption, and the evolving threat landscape – while maintaining control over their most sensitive systems and data.iness. As the ecosystem matures, future trends point toward real-time assurance, orchestration-driven governance, sector-specific adaptation, and continuous measurement of cryptographic resilience.
Summary & Roadmap
In the next section, we will synthesize these insights into a practical roadmap – outlining a step-by-step path to achieving and maintaining crypto-agility in complex enterprise environments.Crypto-agility is moving beyond its initial focus on algorithm substitution and post-quantum readOrganizations that align their strategy with these trends will be better equipped to handle regulatory change, technology disruption, and the evolving threat landscape – while maintaining control over their most sensitive systems and data.iness. As the ecosystem matures, future trends point toward real-time assurance, orchestration-driven governance, sector-specific adaptation, and continuous measurement of cryptographic resilience.
Phase 1: Inventory and Risk Assessment
Objective
Establish a clear baseline of all cryptographic assets, usage patterns, and vulnerabilities across the organization.
Key Actions:
- Establish policies for algorithm agility, key lifecycle management, and hybrid deployments (classical + post-quantum).
- Select libraries and APIs that support algorithm substitution, dual keypairs, and certificate abstraction.
- Define a reference architecture that decouples cryptographic functions from application logic, including interface specifications and control planes.
- Align with emerging industry frameworks (e.g., NIST, CAMM, sector-specific guidance).
Outcome
A defined technical strategy for crypto-agility, aligned with operational and regulatory objectives.
Phase 2: Architecture and Standards Planning
Objective
Define a modular, standards-aligned cryptographic architecture that supports agility and prepares for post-quantum transition.
Key Actions:
- Establish policies for algorithm agility, key lifecycle management, and hybrid deployments (classical + post-quantum).
- Select libraries and APIs that support algorithm substitution, dual keypairs, and certificate abstraction.
- Define a reference architecture that decouples cryptographic functions from application logic, including interface specifications and control planes.
- A defined technical strategy for crypto-agility, aligned with operational and regulatory objectives.
Outcome
A defined technical strategy for crypto-agility, aligned with operational and regulatory objectives.
Phase 3: Pilot Implementation and Integration
Objective
Deploy crypto-agile capabilities in limited, high-impact environments to validate design and operational assumptions.
Key Actions:
- Begin with one or more High-Value Assets (HVAs) identified in Phase 1.
- Implement modular encryption and signing mechanisms using standardized APIs.
- Test hybrid post-quantum algorithms where available (e.g., Kyber + RSA).
- Integrate certificate rotation, key reissuance, and cipher negotiation tools.
Outcome
A validated crypto-agility capability in production, with lessons learned to inform broader rollout.
Phase 4: Automation and Orchestration
Objective
Scale agility across the environment through automation, orchestration, and policy enforcement.
Key Actions:
- Deploy orchestration tools to automate algorithm updates, certificate lifecycle management, and fallback handling.
- Integrate crypto telemetry into existing SIEM/SOAR platforms to enable real-time visibility and alerting.
- Embed cryptographic governance into CI/CD pipelines and infrastructure-as-code (IaC) workflows.
- Enforce policies for cryptographic hygiene and resilience across development and operations teams.
Outcome
A cohesive system for crypto-agility that functions at enterprise scale and supports continuous adaptation.
Phase 5: Continuous Monitoring and Organizational Readiness
Objective
Maintain crypto-agility as a persistent organizational capability – technically, operationally, and culturally.
Key Actions:
- Conduct regular audits and simulations using cryptographic digital twins or testbeds.
- Monitor algorithm usage, telemetry signals, and compliance metrics continuously.
- Provide training and awareness programs for security, development, and risk teams.
- Establish clear ownership for cryptographic governance, with executive visibility and board-level reporting.
Outcome
A resilient cryptographic environment, continuously monitored and ready for future transitions – including post-quantum.
Final Thought
Crypto-agility is not a one-time implementation – it is an operating model for the future of secure systems. The steps above provide a disciplined path forward, beginning with visibility and culminating in sustained control and resilience.
For organizations navigating complex infrastructure, regulatory demands, or limited resources, the most important step is the first: identify your High-Value Assets, assess their cryptographic dependencies, and begin the process of remediation.
In the concluding section, we will explore the current landscape of available solutions – and examine how organizations can evaluate vendors, architectures, and orchestration

Crypto-Agility Solutions: The Current Landscape and the Role of QuSecure
As the urgency surrounding cryptographic modernization intensifies, organizations are increasingly looking for technologies that support crypto-agility. Numerous vendors have introduced tools that address specific aspects of the challenge – from key and certificate management to post-quantum algorithm implementation. However, most of these solutions remain partial in scope, narrowly focused, or operationally siloed.
This section surveys the current landscape of available tools, identifies common limitations, and explains the architectural gaps that have prevented crypto-agility from being fully realized in enterprise environments. We then examine how QuSecure addresses these gaps through an integrated platform designed specifically for cryptographic command and control.
Categories of Available Solutions
1. Hardware Security Modules (HSMs)
Vendors such as AWS (CloudHSM) and Thales (Luna HSM) provide secure, tamper-resistant hardware for cryptographic key storage and processing. These systems are foundational for many enterprise PKI implementations. However, HSMs are limited in their ability to support crypto-agility because they are:
- Hardware-bound, and often difficult to update or reconfigure
- Focused on secure key storage rather than algorithm discovery or policy enforcement
- Lacking visibility into how algorithms are used across distributed services and endpoints
While essential for key protection, HSMs are not equipped to coordinate cryptographic upgrades or manage protocol negotiation across the enterprise.
2. Certificate and Key Lifecycle Management Platforms
Platforms like Venafi and AppViewX offer robust lifecycle management for certificates and keys, including issuance, renewal, revocation, and inventory. These tools improve operational hygiene and reduce the risk of certificate-related outages.
However, their focus is largely at the credential layer. They do not:
- Do not maintain full cryptographic inventories
- Lack automation for key rotation, cipher negotiation, or algorithm upgrades
- Provide limited insight into custom cryptographic implementations
Their functionality is often tightly coupled to access policies, and does not extend to system-wide cryptographic orchestration.
3. Post-Quantum Cryptographic Libraries
Open-source projects such as Open Quantum Safe (OQS), CRYSTALS-Kyber, and Dilithium provide reference implementations of post-quantum algorithms selected by NIST. These libraries represent important technical progress, but they introduce new challenges:
- Deployment requires deep architectural integration and development effort
- There is no standardized orchestration layer to manage hybrid deployments or negotiate transitions
- Most libraries lack telemetry, inventory, and compliance capabilities
In short, while they supply the raw materials of crypto-agility, they do not offer the system-level architecture needed to operationalize it at scale.
4. Zero Trust Platforms with Cryptographic Awareness
Some security vendors – such as Cisco and Zscaler – incorporate encryption policy into their broader Zero Trust frameworks. These platforms may offer control over TLS versions or protocol settings as part of identity and access management policies.
However, cryptographic agility is not their primary focus. These tools generally:
- Do not maintain full cryptographic inventories
- Lack automation for key rotation, cipher negotiation, or algorithm upgrades
- Provide limited insight into custom cryptographic implementations
Their functionality is often tightly coupled to access policies, and does not extend to system-wide cryptographic orchestration.
Common Limitations Across the Ecosystem
The crypto-agility ecosystem remains fragmented. Most available tools address only a subset of the challenge. Common architectural gaps include:
- Siloed capabilities: Tools are specialized by function (e.g., keys, certs, libraries), with little coordination between them.
- Lack of orchestration: Few solutions enable dynamic policy enforcement, protocol negotiation, or automated upgrades across a heterogeneous environment.
- Inadequate inventory and telemetry: Many organizations remain unaware of where cryptographic functions are implemented or which algorithms are in use.
- Limited hybrid support: Tools rarely support seamless transitions from classical to hybrid post-quantum cryptography, particularly across legacy systems.
These limitations lead to complexity, gaps in coverage, and operational delays – especially in environments with diverse architectures, long-lived data, and stringent compliance obligations.
QuSecure’s Architectural Approach
QuSecure was designed to address these challenges directly. Rather than focusing on a single component of cryptographic management, QuSecure delivers a cohesive, end-to-end platform that treats crypto-agility as a security architecture – not just a feature.
The QuProtect platform is structured around three core capabilities:
Recon: Cryptographic Discovery and Risk Visibility
QuSecure’s discovery engine continuously identifies cryptographic assets across the enterprise – cataloging keys, certificates, protocols, cipher suites, and algorithm use.
Key Differentiators:
- Focus on High-Value Assets (HVAs): systems handling the most sensitive data or traffic volume
- Detailed analysis of protocol usage and algorithm configuration
- Identification of non-compliant or deprecated implementations
- Simple interfaces to remediate issues with minimal disruption
Recon provides the foundational visibility needed to guide prioritization and action.
Resilience: Crypto-Agility Orchestration
This is the platform’s command center for automating cryptographic change. The Resilience engine supports:
- Modular algorithm substitution, including hybrid post-quantum support
- Dynamic cipher suite negotiation at runtime
- Integration with CI/CD pipelines and infrastructure-as-code
- Policy-driven enforcement of cryptographic standards across distributed systems
By decoupling cryptographic decisions from application logic, Resilience simplifies transitions, reduces error, and supports continuous modernization.
Reporting: Continuous Assurance and Compliance
QuSecure provides an integrated dashboard for real-time telemetry, audit logging, and cryptographic compliance monitoring. This includes:
- Enterprise-wide cryptographic health scores
- Visualizations of key inventory and algorithm coverage
- Alerts for anomalies or violations of policy
- Exportable reports for internal stakeholders, regulators, or board governance
Together, these capabilities form a continuous loop of discovery, orchestration, and assurance – allowing organizations to maintain crypto-agility not as a project, but as an operational standard.
Designed for Scale, Simplicity, and Security
QuSecure’s platform is software-based and infrastructure-agnostic. It can be deployed over existing systems – on-premise, hybrid, or cloud-native – without requiring extensive rearchitecting. The system is designed for:
- Hybrid cryptography (classical + PQC)
- Multi-domain and multi-vendor environments
- Integration with existing security, identity, and infrastructure tools
Importantly, QuSecure is already in production across sensitive sectors – including defense, telecommunications, and critical infrastructure – demonstrating its readiness for mission-critical environments.
Conclusion
Organizations exploring crypto-agility will encounter a wide range of tools, most of which address individual components of the challenge. These tools can be useful – but none offer the full spectrum of discovery, orchestration, and assurance needed to achieve enterprise-grade agility.
QuSecure stands apart by offering a platform that is purpose-built for crypto-agility at scale: focused on visibility, grounded in standards, and designed for operational simplicity. It enables organizations to move from theoretical readiness to actionable resilience – without disruption, complexity, or delay.
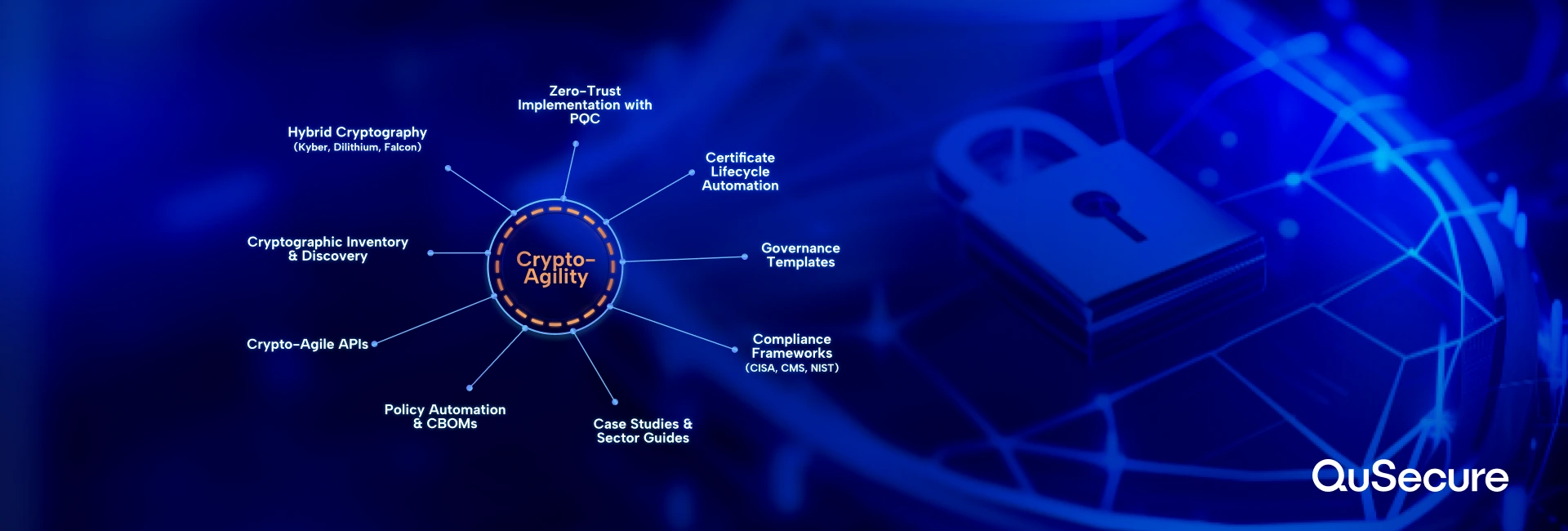
Supporting Posts and Recommended Reading
Each resource is designed to support a specific audience segment: CISOs and CIOs seeking strategic guidance, architects and engineers needing implementation frameworks, and compliance teams tasked with regulatory alignment.
1. A Technical Deep Dive into Hybrid Cryptographic Algorithms
- Why hybridization is critical during the PQC transition period
- Standards in progress (e.g., IETF hybrid key exchange drafts)
- Lacking visibility into how algorithms are used across distributed services and endpoints
- Deployment examples and interop concerns
2. Certificate and Key Lifecycle Management Platforms
- Modular algorithm selection and substitution
- Certificate and key injection via environment configuration
- Integration with external orchestration layers
- Secure negotiation and fallback behavior
3. Comparative Review of Leading Post-Quantum Cryptography Libraries
- Open Quantum Safe (OQS)
- CRYSTALS-Kyber / Dilithium (reference and optimized builds)
- PQClean and liboqs
- Commercial offerings with PQC support (e.g., BouncyCastle, WolfSSL, AWS KMS extensions)
4. Case Study: CMS and Zero Trust with Crypto-Agility
- Their adoption of Zero Trust principles
- Deployment of crypto discovery tooling
- Transitioning away from SHA‑1 and RSA-1024
- Lessons learned in integrating crypto-agility into a large federal environment
5. Crypto Tooling: Integrating Vault, PKI Automation, and Inventory
A guide to building and integrating supporting infrastructure to enable crypto-agility, including:
- Secrets management with HashiCorp Vault or Azure Key Vault
- Certificate issuance via ACME, EJBCA, or Cert-Manager
- Using inventory tools (e.g., Recon) to maintain visibility
- Workflow automation with Terraform, Ansible, or Kubernetes operators
6. Governance and Policy Templates for Cryptographic Agility
Crypto-agility cannot be sustained through tooling alone – it must be backed by governance. This resource includes:
- Sample policies for cryptographic algorithm lifecycle management
- Compliance checklists for FIPS, NIST SP 800-131A, and NSA CNSA 2.0
- Role-based responsibilities for cryptographic ownership
- Audit log requirements and incident playbook templates
Editorial Note
Additional resources will be developed over time in alignment with evolving standards, sector-specific use cases, and client feedback.












