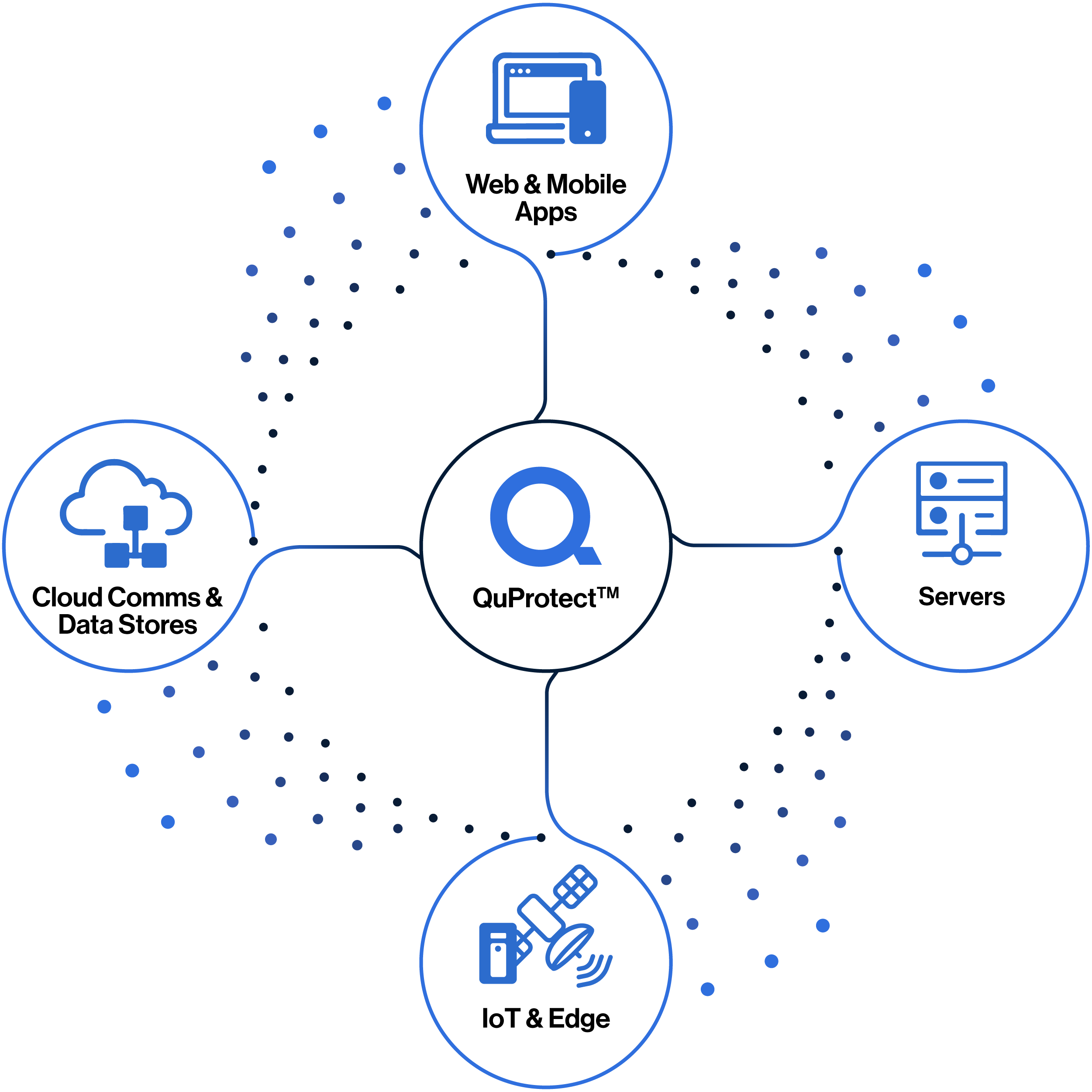
An all-in-one-software-based solution that provides quantum protection for critical data anywhere it travels. Secure your valuable data assets from today’s store now, decrypt later attacks and gain new controls over your cryptography.
QuSecure Honored as Global Product Leader in Post-Quantum Cryptography by Frost and Sullivan