Post-Quantum Cryptography Made Simple
See your vulnerabilities. Secure your systems. Showcase your compliance.
RSA, ECC, and other widely used algorithms are on borrowed time.
The Problem
Most organizations don’t know what cryptography they’re using, where it’s deployed, or whether it can survive what’s coming.


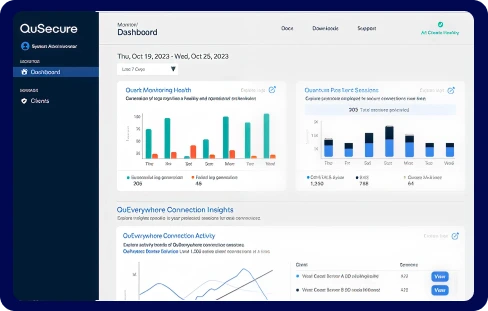
QuProtect

-
The Solution
It delivers real-time discovery, automated remediation, and continuous cryptographic visibility – in a single unified platform.
See
in Action
One Platform. Three Core Capabilities.
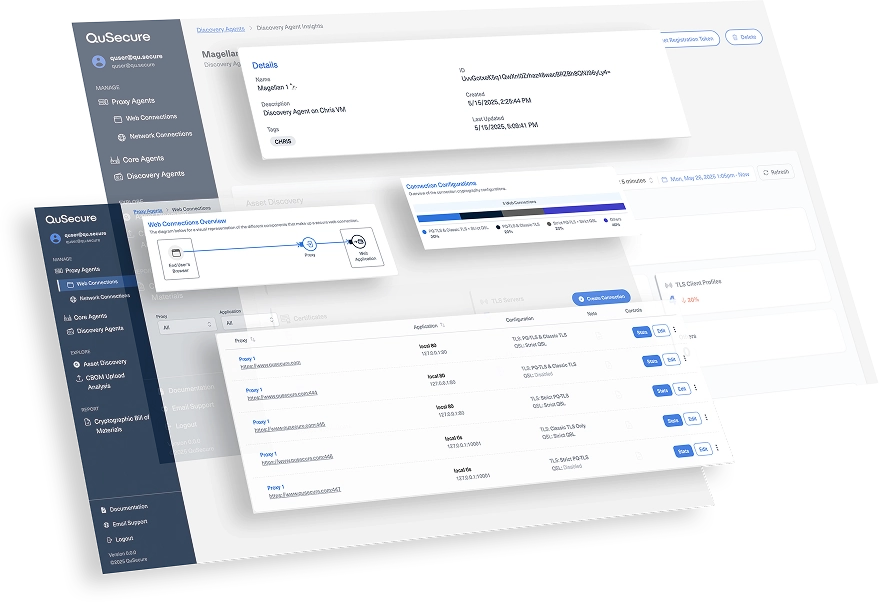
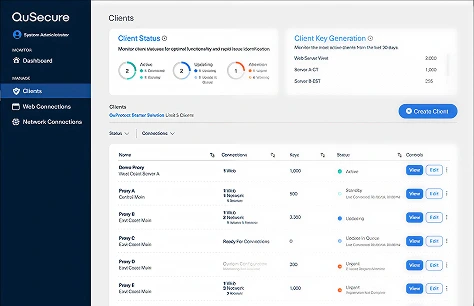
QuProtect Recon –
Discovery Engine
- Instantly scans your infrastructure - network, cloud, applications, endpoints
- Creates a live inventory of all cryptographic assets and algorithms
- Flags vulnerable, deprecated, or out-of-policy cryptography
- Updates in real time to track posture as environments evolve
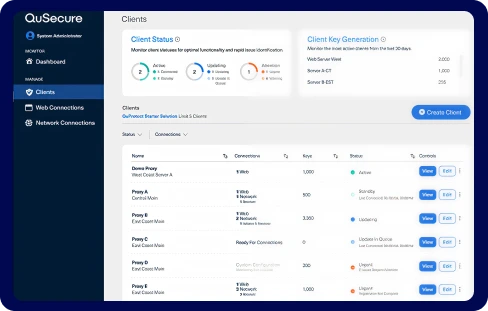
QuProtect Resilience –
Crypto-Agility Orchestrator
- Seamlessly upgrades encryption protocols across devices and systems
- Enables scheduled or on-demand transitions to post-quantum algorithms
- One-click remediation - no downtime, no code rewrites, no rip-and-replace
- Built to support NIST-approved PQC algorithms
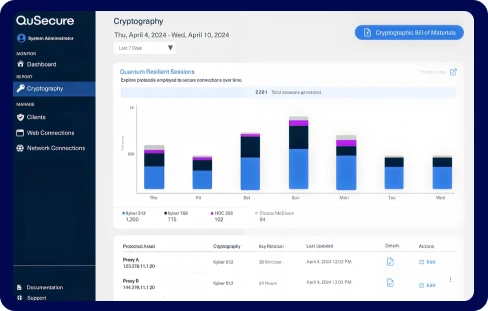
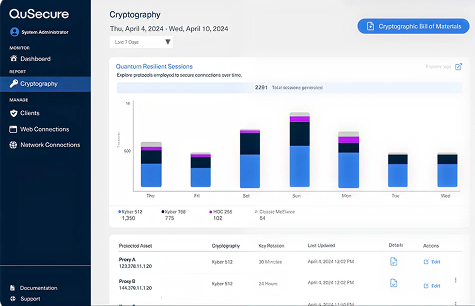
QuProtect Reporting –
Real-Time Compliance Engine
- Automatically generates CBOM (Cryptographic Bill of Materials)
- Visualizes cryptographic posture trends and risks
- Tracks alignment to NIST, NSM-10, EO 14028, and OMB M-23-02
- Produces audit-ready reports for CISO, CIO, and compliance teams
The moment the threat hits,
responds
No delay. No disruption.
Built For Security and Compliance Leaders
QuProtect R3 is trusted by those who cannot afford to fall behind.
Whether you’re a CISO protecting critical infrastructure, a program manager preparing a federal agency for post-quantum migration, or an enterprise architect modernizing your crypto stack – R3 gives you full control and clear visibility.

See
in Action
Schedule a live demo to see the only platform that can help you:
- Discover what’s deployed
- Remediate risk in real time
- Report compliance with confidence
Why
Stands Out
Legacy Scan Tools
Manual Methods
Legacy Scan Tools
- Full Asset Visibility
- Partial
- Live, End-to-End
- PQC Algorithm Detection
- Built-In
- CBOM Generation
- Real-Time
- Continuous Monitoring
- Manual
- Always-On
- Compliance Framework Support
- Partial
- Limited
- NIST, NSM-10 Ready
- Remediation / Crypto-Agility
- Native
- Deployment Time
- Months
- Weeks
- Days
See
in Action
Ready to Take Command?
You’ve seen what’s coming. Now take control before quantum breaks everything.
With
, you can:

Discover what’s
deployed

Remediate risk in
real time
