By Rebecca Krauthamer, CEO of QuSecure
For years, security leaders have been told that preparing for post-quantum cryptography (PQC) would take half a decade, cost tens of millions of dollars, and require deep in-house expertise. At QuSecure, we believe that this narrative has slowed progress and left organizations uncertain about how to move forward. With the launch of QuProtect R3, we are demonstrating that cutting-edge technology will enable encryption modernization to be achieved faster, more affordably, and with far less disruption than previously thought possible.
The Debate Is Over
Yes, it is true that the quantum threat is real and harvest-now, decrypt-later attacks are underway, but this is only a small fraction of the story. In truth, this attack has been present since the beginning of cryptanalysis and will continue well beyond the transition to the new PQC algorithms.
The real story is that the debate about what to do is now definitively settled. With NIST standardization finalized last year, the regulatory and compliance landscape has shifted decisively. Federal agencies, banks, insurers, telecoms, and energy companies have already begun executing on their quantum security roadmaps.
It is no longer controversial whether organizations need to act, or even how to proceed with adoption of post-quantum cryptography standards. Today’s central question is how to migrate without tearing out infrastructure that has been carefully built over decades, without relying on armies of subject matter experts, and without draining budgets for years on end. The deadlines are clear. One of the nearest arrives just over a year from now: by January 1, 2027, vendors selling into national security systems must be CNSA 2.0 compliant. Similar deadlines are approaching across industries worldwide. Migration is no longer optional and is already underway at many F500 and PubSec organizations.
The First Questions Every Organization Asks
In the early stages of post-quantum migration, every CISO and board asks the same three questions:
- How much will this cost
- How many people will it require
- How long will it take
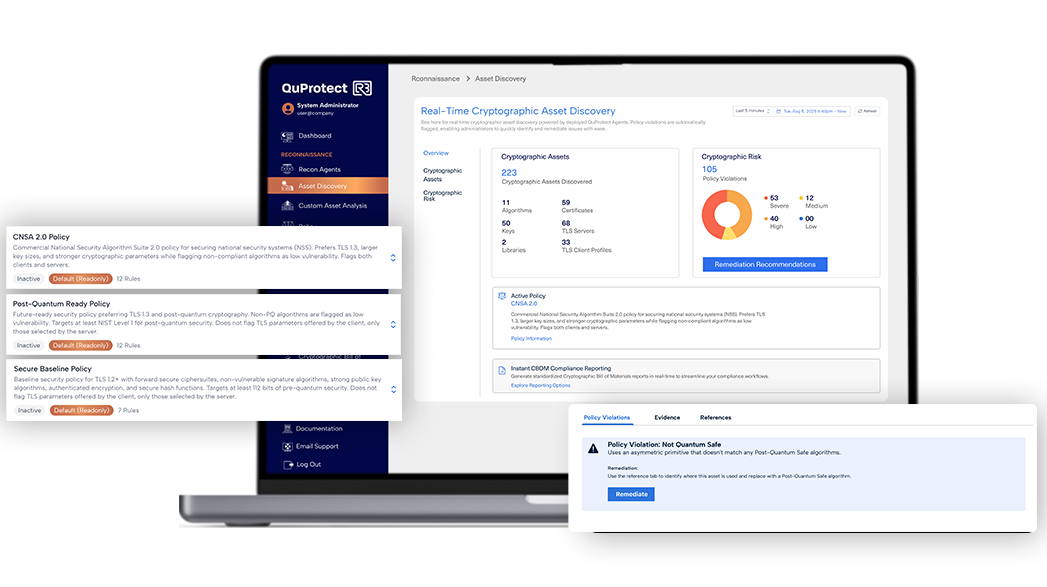
QuProtect R3 was purpose built to allow those answers to come faster and more clearly than ever before. R3 focuses on solving encrypted communications from the network level allowing for the most flexible and backwards compatible architecture in production today. Our Reconnaissance module can be deployed in as little as a week, even for large enterprises. It provides a live and continuous inventory of cryptographic debt, automatically highlights the riskiest assets, and produces a clear and actionable remediation roadmap custom to the needs of each enterprise. Instead of relying on inflated multi-year estimates, leaders can act today and base decisions on hard data from their own environments.
| Outdated Migration Methods | Today’s Gold Standard | |
| Cost | Discovery: 6-7 figures
Migration: Large leading organizations with complex infrastructure and cryptographic debt have shared estimates exceeding $100M for full migration. Subsequent Discovery, Inventory and Migration: Same as above |
Discovery: Free
Migration: Straightforward, predictable pricing at a small fraction of legacy migration cost. Subsequent Discovery, Inventory, and Migration: zero additional cost |
| Staffing Requirements | Hiring specialized in-house encryption management teams to create Cryptographic Centers of Excellence (CCoE’s), or engaging large services-based consulting teams. | Your CISO should be empowered to set policy and your Network Security Administrator should be empowered to manage the administration of policy and reporting without large teams with specialized cryptography knowledge. |
| Time | Discovery: Up to 24 months
Migration: 5+ years for full dedicated migration with substantial rip-and-replace (in many cases will not be completed as priorities shift) Subsequent Migrations: 3-7 years |
Discovery: less than one year
Migration: Phased and legacy compatible migration prioritizing the most valuable assets to the organization Subsequent Migrations: Instantaneous and Policy-Based via Crypto-Agility |
Discovery as a Launchpad, Not a Dead End
Too many organizations have spent hundreds of thousands of dollars on cryptographic inventories that languish and never translate into action. Discovery inadvertently becomes the end state instead of the beginning. QuSecure takes a different, more complete, 360 view of the cryptographic lifecycle. We built Reconnaissance into our R3 platform to make discovery a launchpad for migration.
With Recon, security teams gain rapid visibility into modern, legacy, and cloud systems, and can generate a Cryptographic Bill of Materials (CBOM) in minutes. Most importantly, that data feeds directly into remediation and reporting, enabling a bias for action and minimizing risk of transitioning between disparate tools. Discovery should not be where migrations stall. It should be where they accelerate.
One Platform, Three Capabilities
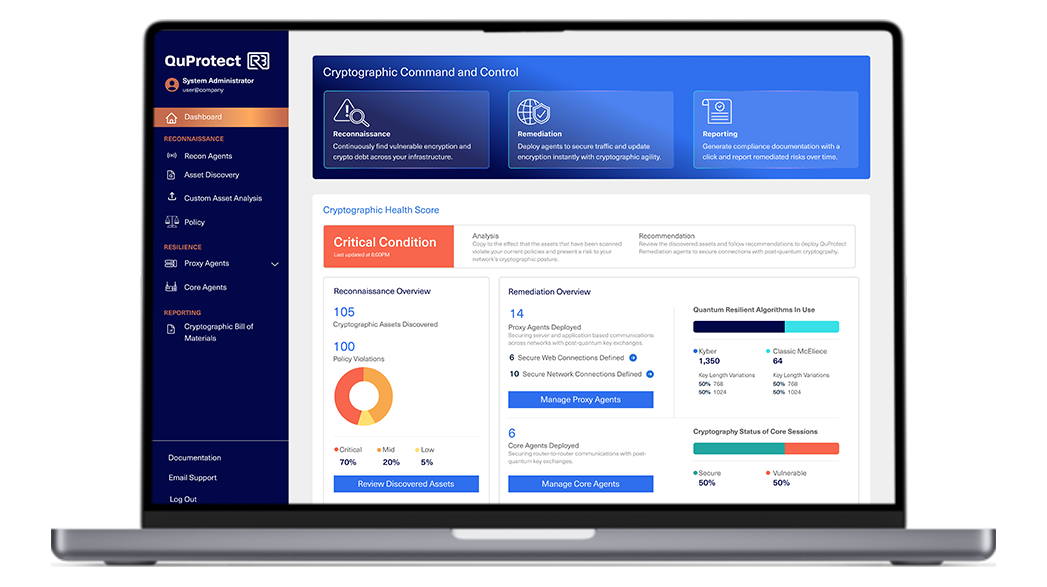
QuProtect R3 is the only production-ready platform that unifies:
- Reconnaissance: Continuous discovery and inventory, turning inventory from academic exercise into actionable, facilitating not just visibility but the pipeline for automating migration. Free to qualifying organizations.
Request your free Recon deployment today
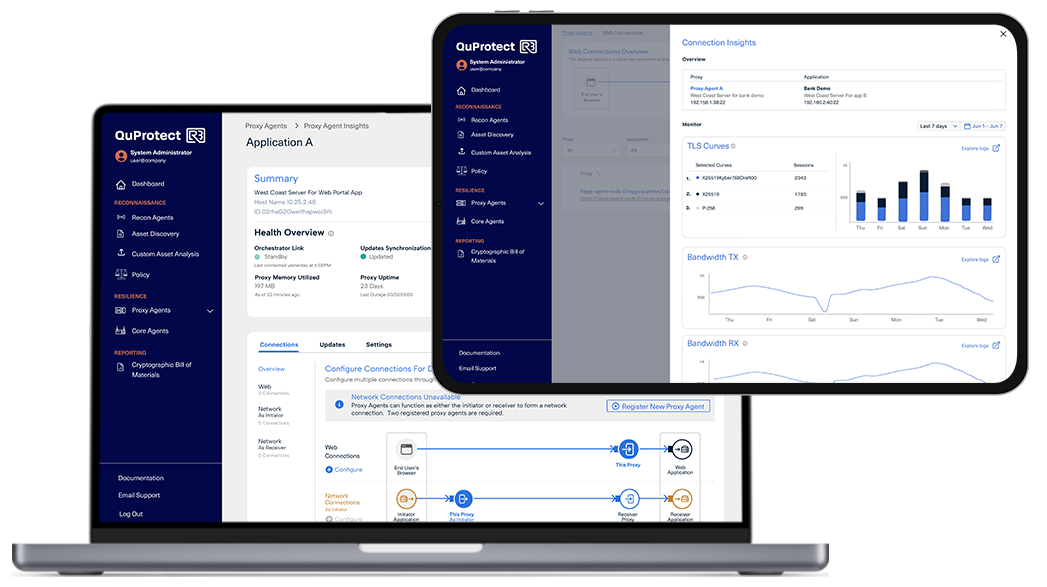
- Resilience: Active mitigation that enables crypto-agility across both modern and legacy systems without disruption
Learn why the architecture that QuSecure pioneered is now considered best practice with a complimentary copy of Forrester’s Architect’s Guide to Quantum Security
- Reporting: Real-time insights and one-click CBOMs that simplify compliance with your organization’s custom policy, or pre-defined policies like CNSA 2.0 and more.

Request a demo or Download our Whitepaper
This integration ensures that enterprises can move from discovery to remediation to compliance within a single system.
Orchestration at Scale
Marcos Christodonte II, SVP Global CISO at CDW, put it well:
“Orchestration is the only way to manage complexity at scale. PQC requires the same approach: centralized discovery, automated workflows, and unified control across IT and OT. This is not a future state. QuSecure shows that this orchestration framework is agency-ready right now.”
Proven Protection
QuSecure pioneered orchestrated crypto-agility, and today we have more real-world deployments than any other provider. We are proud to work with the U.S. Army and Air Force, leading financial institutions, global cloud providers, and major players in telecommunications and energy.
With QuProtect R3, we are extending that leadership. The platform addresses both the compliance mandates of today and the security threats of tomorrow. Customers report reducing discovery timelines from months to days and avoiding nine-figure cost projections associated with traditional approaches. What once looked like a 5+ year journey can now be undertaken with clarity, speed, and control.
Thank You to the Incredible QuSecure Team
QuProtect R3 is the result of extraordinary teamwork. I am deeply grateful to the QuSecure team whose vision and execution made this possible, and to our customers and partners for trusting us to safeguard their most critical systems.
The migration era has begun. The deadlines are here. With QuProtect R3, you can move forward with clarity, confidence, and control.
See your organization’s CBOM in days, not months.











