See Everything.
Miss Nothing.
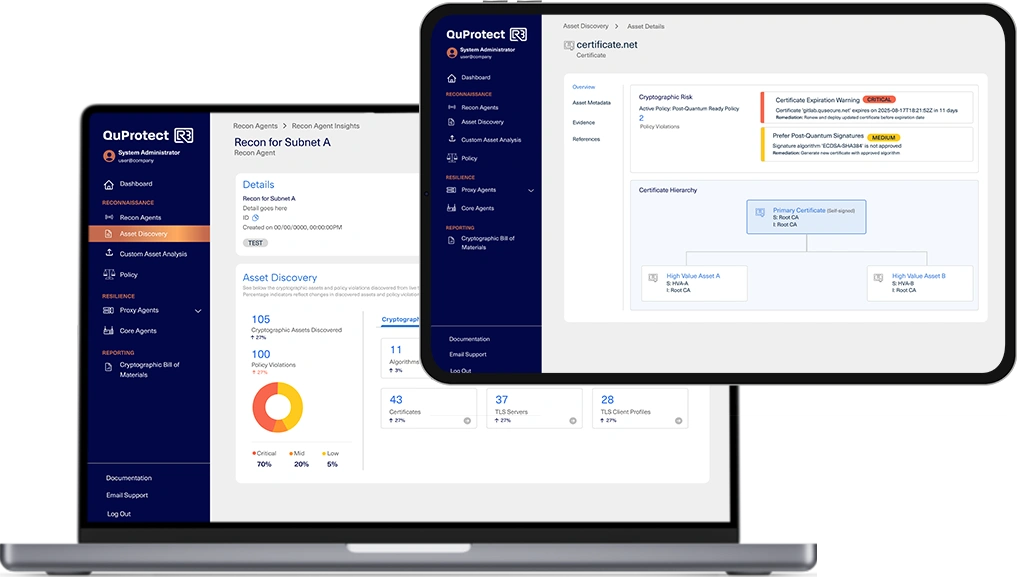
QuProtect Recon delivers a live, automated inventory of cryptographic assets across your network – helping you uncover vulnerabilities, eliminate blind spots, and accelerate quantum readiness.
You Can’t Secure
What You Can’t See
Most organizations have no visibility into what cryptographic algorithms are actually running across their infrastructure. Encryption decisions made years ago, or inherited from M&A, vendors, or legacy code quietly remain in production – creating unseen risk and a MASSIVE compliance gap.
Manual discovery processes are slow, expensive, and outdated. Security teams often rely on command-line forensics, labor-intensive fieldwork, and fragmented spreadsheets. These methods take months, introduce human error, and fail to keep up with dynamic environments.
The Stakes Have Never Been Higher
Quantum computing is no longer theoretical. Federal directives like Executive Order 14028 and NSM-10 are raising the bar on cryptographic compliance.
The bottom line: Most organizations don’t know what encryption they have, where it lives, or whether it’s putting them at risk.
QuProtect Recon changes that by turning uncertainty into clarity, instantly.

The Problem We Solve
Automated, Continuous Cryptographic Discovery
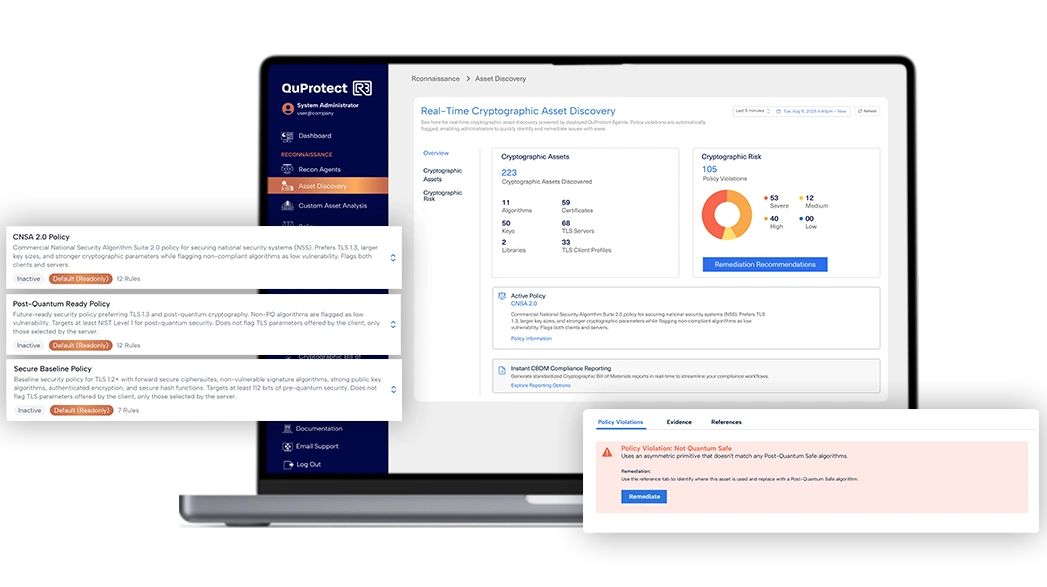
QuProtect Recon scans your environment – continuously and automatically – to detect, identify, and inventory cryptographic assets across your network.
Full-Stack Visibility
Scan every layer - routers, servers, endpoints, apps, cloud, apps, and network infrastructure

Security Without Obstruction
Eliminate hidden weaknesses in your crypto stack
Algorithm-Level Detection
Identify exactly which encryption algorithms (RSA, ECC, PQC-ready) are actually in use across network assets
Policy Compliance Monitoring
Instantly flag out-of-policy, deprecated, or vulnerable algorithms to assess cryptographic debt
Live Cryptographic Inventory
Real-time updates ensure accuracy as your environment changes

What Used to Take Months of Fieldwork, Recon Delivers in Minutes
Without the Risk of Human Error
Key Functions
Reconnaissance
Problem: Cryptography is spread across dozens to hundreds of applications, vendors, and systems; it’s difficult to know what you have, much less manage it. Operational configuration may drift from secure defaults or take shortcuts with self-signed certificates, vendor certificates, or even no certificates.
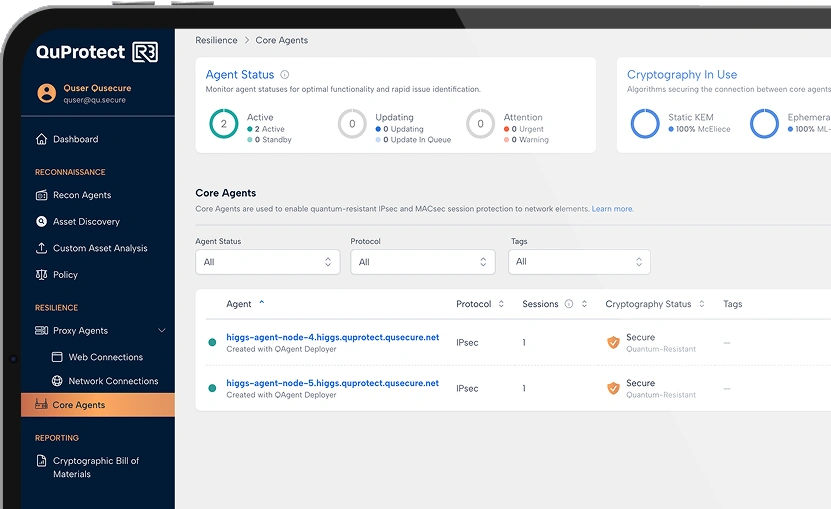
Solution: Lightweight agents monitor live network traffic, creating a browsable inventory of cryptographic protocols, ciphersuites, and certificates observed in real-time.
Why It Matters Now
Post Quantum Compliance Starts Here!
Recon simplifies this transition.
- Establish a quantum-readiness baseline
- Avoid rip-and-replace chaos
- Prove system-of-record for cryptographic asset management
- Provide an evidence trail for auditors, regulators, and C-suite oversight
- Aligned to NDA CNSA 2.0, NIST PQC, IL5+/FedRAMP, CMMC 2.0
- Upload existing inventory for jump start to remediation
With Recon, compliance isn’t a checkbox. It’s a strategic advantage.
The Foundation for Crypto-Agility
Discovery Is Step Zero
You can’t migrate to PQC or deploy crypto-agility without first knowing what you have. You can’t rekey, reconfigure, or remediate what you can’t see.
Recon makes that possible – and frictionless.

QuProtect Recon lays the foundation for true cryptographic agility:
- It tells you exactly where legacy cryptography lives.
- It shows you what’s compatible with post-quantum upgrades.
- It empowers you to orchestrate algorithm transitions with precision.
It’s not just a scan. It’s a strategy.
Recon is how you future-proof your cryptographic security stack.
Who Uses Recon
Built for Security Leaders and Compliance-Driven Teams

Recon is the trusted discovery foundation for any organization serious about securing its future.
Designed for CISOs, security architects, compliance officers, or federal program managers who need real-time insight into their cryptographic posture.
Whether you’re preparing for a PQC migration, responding to new regulations, or building a Zero Trust architecture, Recon becomes your discovery backbone.
Don’t Wait for a Breach or a Deadline
Schedule a live demo to see how QuProtect Recon delivers cryptographic visibility in seconds-not months.
Let Recon power your discovery. Let QuProtect secure your future.