Complimentary Access: “The Architects’ Guide to Quantum Security, Forrester Research, 2025”
The world is talking about QuSecure. Explore press releases, analyst reports, award wins, and media features that reflect our leadership in post-quantum cybersecurity.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod tincidunt ut laoreet dolore magna aliquam erat volutpat. Ut wisi enim ad minim veniam, quis nostrud exerci tation ullamcorper suscipit lobortis nisl ut aliquip ex ea commodo consequat. Duis autem vel eum iriure dolor in hendrerit in vulputate velit esse molestie consequat, vel illum dolore eu feugiat nulla facilisis at vero eros et accumsan et iusto odio dignissim qui blandit praesent luptatum zzril delenit augue duis dolore te feugait nulla facilisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod tincidunt ut laoreet dolore magna aliquam erat volutpat. Ut wisi enim ad minim veniam, quis nostrud exerci tation ullamcorper suscipit lobortis nisl ut aliquip ex ea commodo consequat. Duis autem vel eum iriure dolor in hendrerit in vulputate velit esse molestie consequat, vel illum dolore eu feugiat nulla facilisis at vero eros et accumsan et iusto odio dignissim qui blandit praesent luptatum zzril delenit augue duis dolore te feugait nulla facilisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod tincidunt ut laoreet dolore magna aliquam erat volutpat. Ut wisi enim ad minim veniam, quis nostrud exerci tation ullamcorper suscipit lobortis nisl ut aliquip ex ea commodo consequat. Duis autem vel eum iriure dolor in hendrerit in
Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod tincidunt ut laoreet dolore magna aliquam erat volutpat. Ut wisi enim ad minim veniam, quis nostrud exerci tation ullamcorper suscipit lobortis nisl ut aliquip ex ea commodo consequat. Duis autem vel eum iriure dolor in hendrerit in
Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod.
Posted on April 19, 2022, by Rebecca Krauthamer in Best Practices Click here to read the full article published in Best Practices for Information Security Solutions Review As part of Solutions Review’s Premium Content Series—a collection of contributed columns written

Q-Day will arrive when a quantum computer can decipher the asymmetric encryption protecting our vital systems. Our current encryption standards protect our bank accounts, financial markets, and most of our infrastructure, not to mention the logistics/supply-chain management system in
Listen to the full podcast here – https://www.protiviti.com/us-en/podcast/achieving-crypto-agility Crypto-agility measures a company’s ability to enable rapid adaptations to cryptography. This includes using new cryptographic primitives and algorithms without making disruptive changes to a system’s infrastructure. Every company will need to

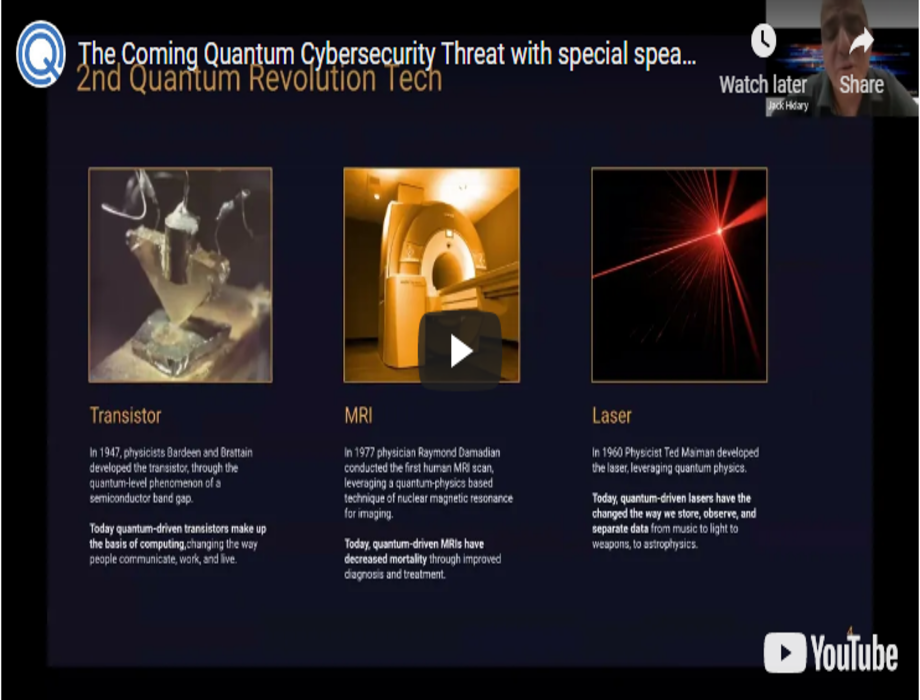
On Wednesday, February 2, 2022, QuSecure held a hard-hitting online seminar about The Coming Quantum Cybersecurity Threat! We covered existing and emerging cybersecurity threats and practical and currently available post-quantum cybersecurity solutions to thwart quantum and classical attacks on our
A new report by the consulting firm Booz Allen Hamilton on China’s steady push for quantum supremacy is making waves on Capitol Hill and in board rooms across the country. This isn’t surprising. The report’s conclusions echo what we’ve repeatedly

A growing concern among US government officials is the development of Cryptographically Relevant Quantum Computers (CRQCs): quantum computers capable of breaking current cryptography. Dustin Moody, a mathematician at the National Institute for Standards and Technology (NIST), warns that the possibility

In product development, many times cost is more of a concern than security. With the Internet of Things (IoT), devices are providing an increasing large attack vector for hackers to enter networks. Many IoT devices use cloud-based servers to communicate

Reference Article: https://www.scmagazine.com/analysis/encryption/the-government-is-close-to-picking-quantum-resistant-encryption-standards-now-it-must-plan-for-what-to-do-if-they-fail The National Institute of Standards and Technology (NIST) works to provide the strongest cryptographic standards and is trying to stay ahead of the quantum computer threat. Discrete logarithms, elliptic curves, and integer factorization are basis of cryptographic

Reference Article: https://www.forbes.com/sites/arthurherman/2022/01/21/the-biden-white-house-gets-quantum-right-at-last/?sh=6319d643598a On Wednesday, January 19th, President Biden signed a National Security Memorandum on Improving the Cybersecurity of National Security, Department of Defense, and Intelligence Community Systems. This is the first time that any White House national security directive

The Quantum Daily (TQD) has released a list of 52 women working as engineers or in positions requiring technical competence in quantum computing (QC) startups. The list, as usual, is non-exhaustive — it’s just a general map of what it

QuSecure, Inc.
1900 South Norfolk Street
Suite 350
San Mateo, California 94403