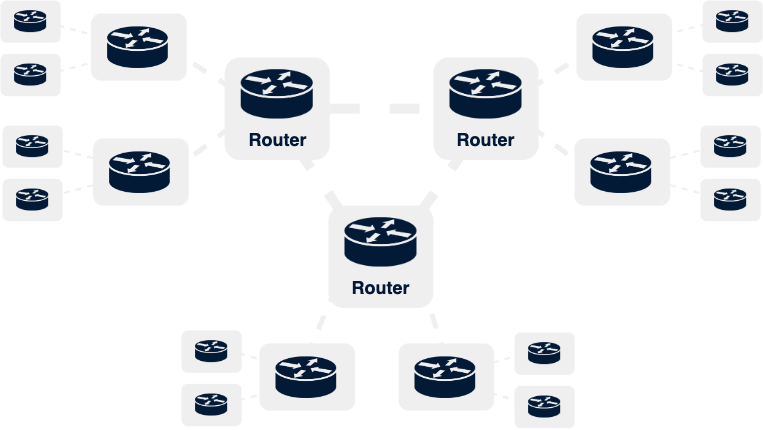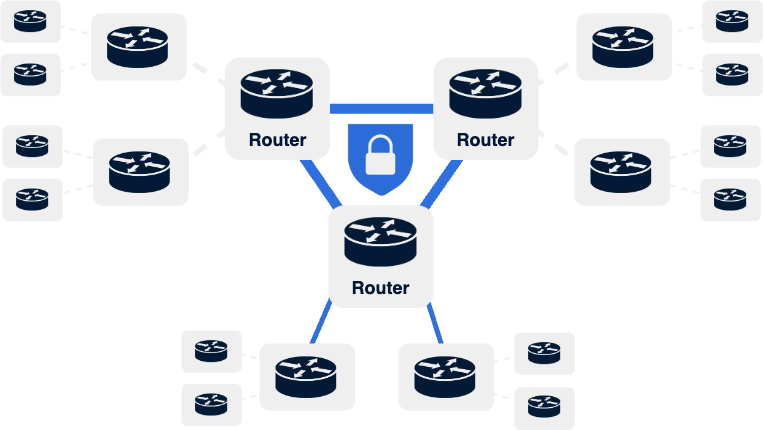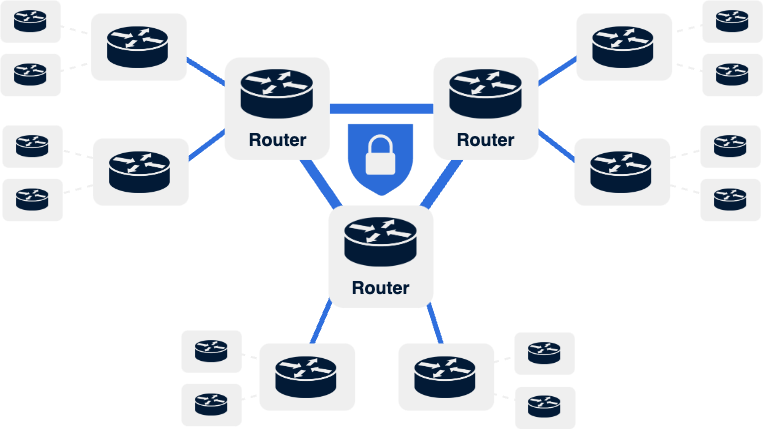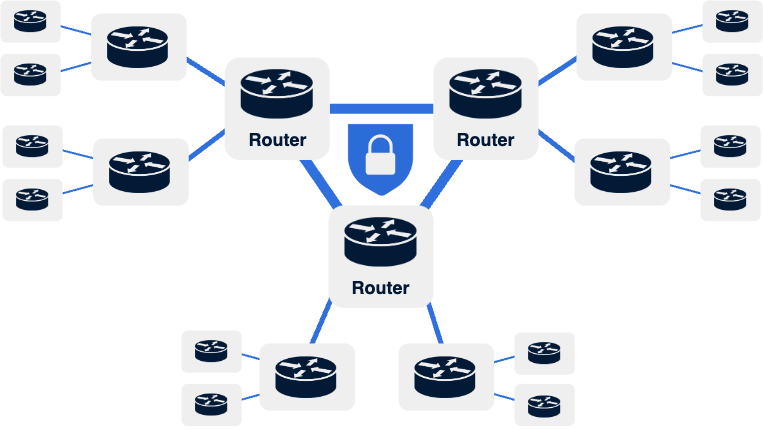
Internet Protocol Security (IPsec) is the workhorse network encryption protocol of the modern enterprise. It enables the creation of virtual private networks that provide confidentiality, integrity, and authenticity protections for data transiting between data centers, branches, and the cloud. As these critical links between sites increasingly make use of untrusted networks such as the public Internet for transport, they are the most vulnerable to adversarial intrusion and, by extension, the quantum threat.
QuSecure Honored as Global Product Leader in Post-Quantum Cryptography by Frost and Sullivan