QuSecure Honored as Global Product Leader in Post-Quantum Cryptography by Frost and Sullivan
The guide below overviews the evolution of digital cryptography starting in the 1970’s. While cryptography upgrades are not new, they have always been challenging and introduce risk. The joke in the industry is, “Find single-DES. Where is DES hiding? DES was cracked in 1998.” The joke being that it is hard to play whack-a-mole with all pointwise instances of encryption. This is why the upgrade to quantum-safe encryption is not about quantum at all, it’s about cryptographic agility and the ability to hot-swap and layer algorithms, so you are never caught flatted again.
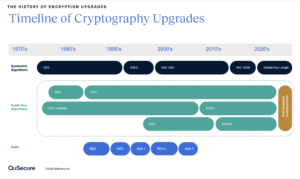
Quantum computing, as well as maturing AI capabilities represent the end of an era. This migration isn’t just to post-quantum cryptography, or another algorithm. It’s about migration to cryptographic agility – to full visibility and control over the cryptography in use in your network. It means gaining the ability to push-button swap out algorithms, key lengths, key rotation frequency, and more without disruption to your existing systems or, in fact, the need to launch new satellites.
In 2016, NIST initiated the call for quantum-resilient cryptosystems, the algorithms that would take us forward in a post-RSA, post-ECC world. A lot of smart people have been working tirelessly since then, but the ecosystem was relatively quiet for the next 8 years.
Then in late 2021, a briefing was making its way around DC alerting policy makers to the coordinated efforts and investments being made into quantum internationally, especially by China. The quantum program has been described as China’s Manhattan Project.
Policy makers began to understand that this upgrade cycle is not like Y2K. We don’t have until 11:59PM the night before quantum comes of age to get it right. Data is being harvested now, and therefore the time to act is now.
In January 2022, the United States were hit with the first executive memo mandating the start of the migration to quantum resilient encryption. Shortly after we at QuSecure were called into deploy what we were told was the first test deployment of PQC within the DOD, with Red Hat as our enabling foundations.
In May of 2022, a second executive memo followed.
Mid-year, NIST released it’s new provisional standards for quantum resilient cryptography.
In November, the Office of Management and Budget released guidance for complying with the mandates
And in December, the Quantum Computing Cybersecurity Preparedness Act was voted, almost unanimously into law.
2023 is the year we are all meant to start adopting systems that comply with the new mandates. Help us secure the future, today. Schedule a call with our team to see how easy it is to get started with quantum-resilient protection.
Click Here to download the graphics