Upgrade Your Cryptography
Not Your Infrastructure
See your vulnerabilities, secure your systems, showcase your compliance.
The Only Fully Integrated, Production-Ready Platform for Discovery, Remediation, and Reporting
QuProtect Reconnaissance
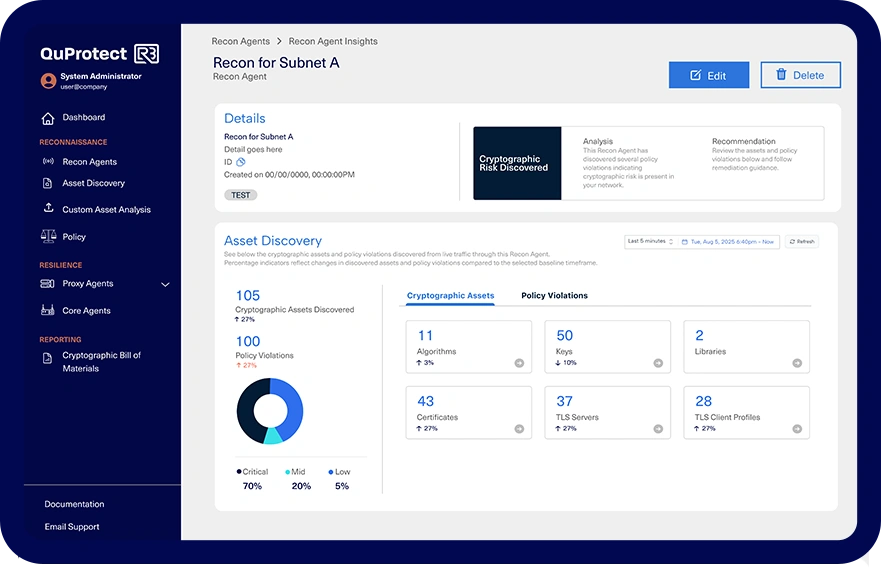
Continuous Discovery
Gain a comprehensive, live inventory of crypto in use to secure network data in transit. Leverage QuProtect Reconnaissance for custom assessments that easily highlight out-of-policy or vulnerable algorithms, providing actionable insights to strengthen your security posture.
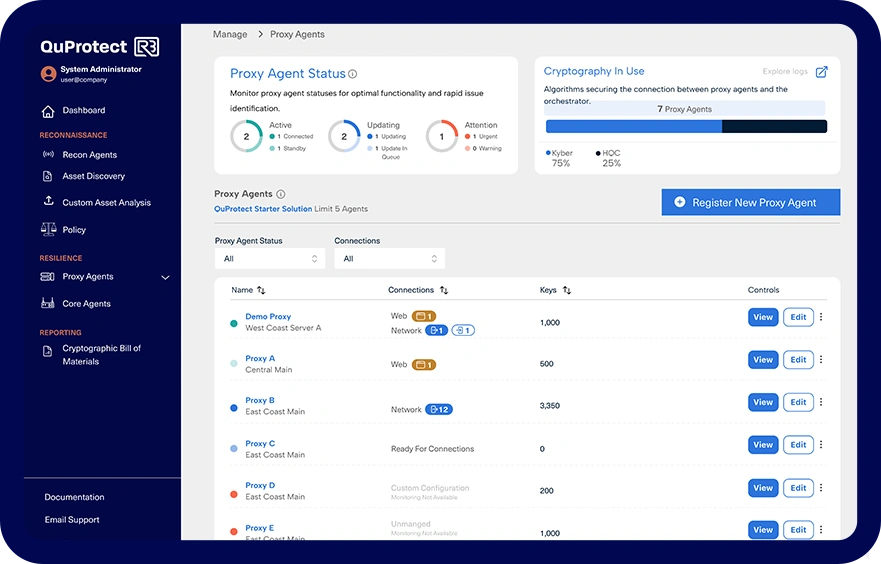
QuProtect Resilience
Active Remediation
Deploy cryptographic protection across your entire network with ease using QuProtect Resilience. Execute crypto-agility to instantly update encryption across all devices and systems, ensuring adaptive defense without disruptions or code changes, even when algorithms are compromised or new standards emerge.
QuProtect Reporting
Real-Time Reporting
Streamline compliance with QuProtect Reporting, offering on-demand visibility and control. Access Cryptographic Bill of Materials (CBOM) to ensure compliance with evolving standards like NIST, FIPS, and GDPR, while maintaining full transparency over your cryptographic inventory.
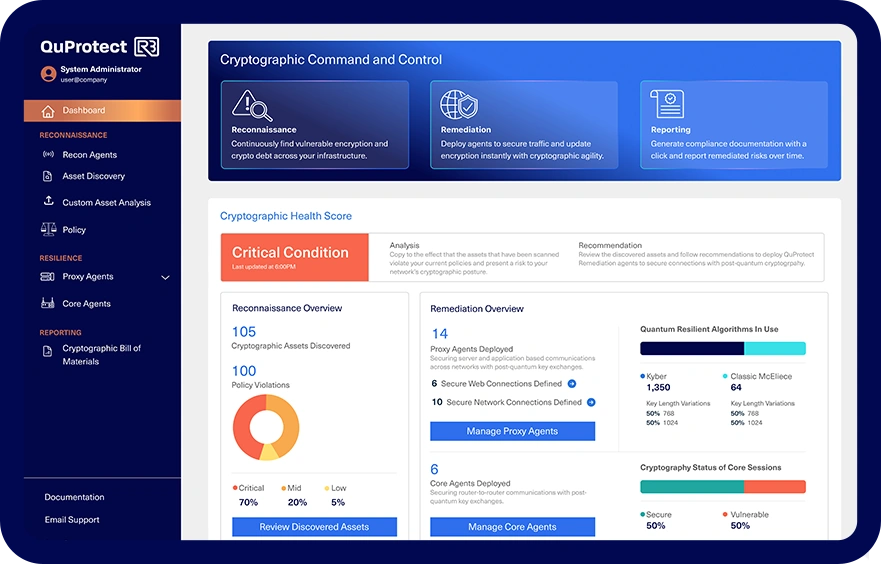
The Control Plane for the Post-Quantum Era

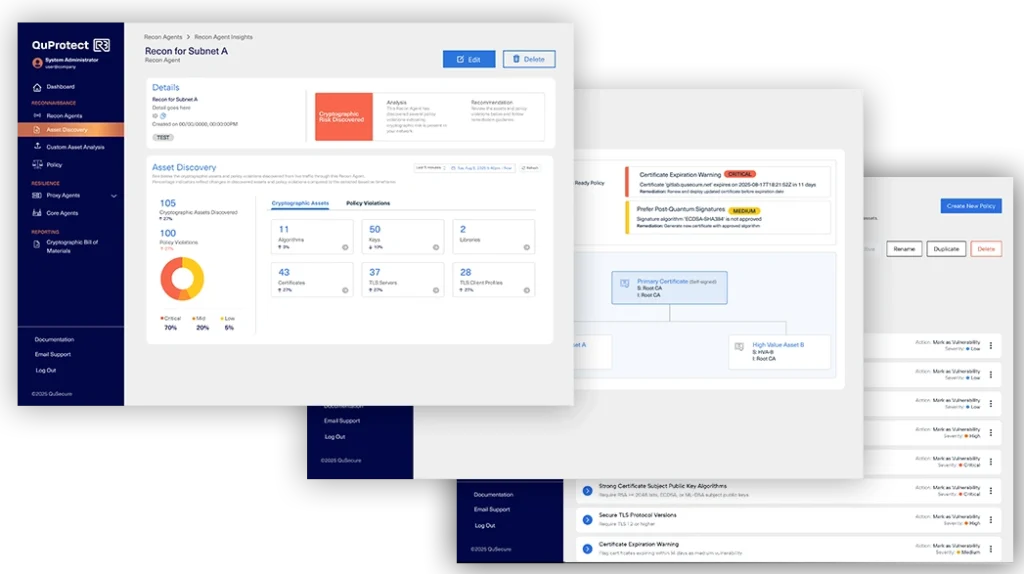
Gain an evergreen inventory of cryptographic assets across cloud, on-prem, air-gapped, and legacy systems in days, not months. See what’s actually protecting your data in real-time, not just what’s configured in files.
Discovery
The only fully integrated platform for cryptographic command and control – from discovery to remediation and reporting. QuProtect R3 delivers visibility and control over your crypto landscape without breaking what works.
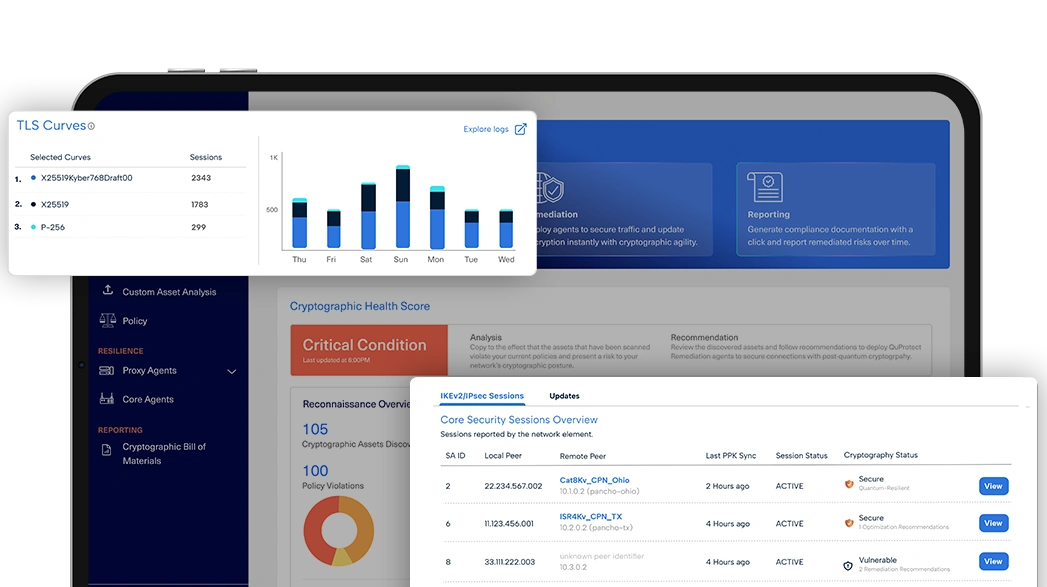
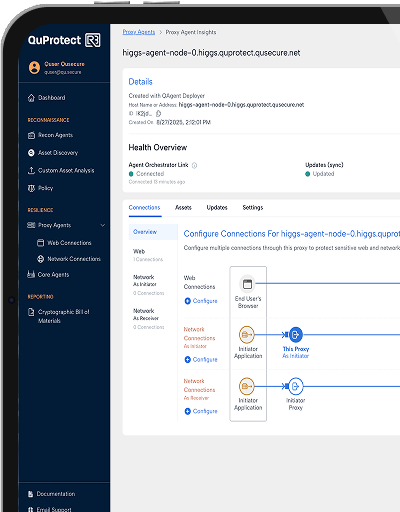
Crypto-agility & Remediation
Rapidly remediate cryptographic risk with clicks – not code changes, no rip-and-replace required. Seamlessly transition to post-quantum cryptography and enhance zero-trust security across all systems.
Rapidly remediate cryptographic risk with clicks – not code changes, no rip-and-replace required. Seamlessly transition to post-quantum cryptography and enhance zero-trust security across all systems.
Automated Compliance & Reporting

Elevate Security. Optimize Value.
Consolidate products, maximize value, and improve business continuity. See why enterprise and government choose the QuProtect platform over other security vendors.
Securing the Best of the Best
Marcos Christodonte II, SVP Global CISO, CDW
Max Everett, CISO, former CIO at the Department of Energy and the White House

“Cryptography plays a crucial role in banking, securing processes such as payments, digital interactions with customers and communications with market infrastructure… This project, in collaboration with Accenture and QuSecure, has allowed us to explore the impact of the adoption of post-quantum cryptography technologies on the bank’s infrastructure.”
Joan Puig, Group CISO of Banco Sabadell
“Thrilled to see QuSecure’s groundbreaking R3 Reconnaissance and crypto agility solution redefining the journey to quantum security. What was once a complex, long-standing challenge is now being solved through seamless and continuous migration.”
Helena Handschuh, Security Technologies Executive, Former Rambus Fellow
Aaron Wentzel, CPO, Translational Analytics & Statistics

“With ever-evolving use cases, security requirements, and operational complexities, cryptography and crypto-agility will play a much bigger role for organizations in the future. In the context of PQC and beyond, QuSecure brings a disruptive approach to how cryptography is deployed and managed. Coupling full control with simplicity, the company’s offering uniquely positions itself in the ecosystem of cryptographic modernization.”
Recognized as Global Post-Quantum Cryptography Industry Product Leader by Frost & Sullivan, 2024
Natalie Gregory, Vice President at Carahsoft
Tom Patterson, Emerging technology lead at Accenture Cybersecurity.
“Having built GTM strategies across multiple sectors, QuSecure’s platform represents exactly what enterprise customers demand: a single, comprehensive solution that eliminates vendor sprawl while accelerating time-to-value. They’ve turned PQC from a future threat into an immediate opportunity for competitive advantage.”
Chris Thilburg, CEO Evolutia
“The Architect’s Guide to Quantum Security,” Forrester Research, 2025.
The Standard in Security Excellence
Tried and trusted by the industry’s leading authorities, analysts, and associations.
Modernize Without Disruption
Eliminate cryptographic debt with QuProtect R3 the first end-to-end platform for discovery, remediation, and compliance.